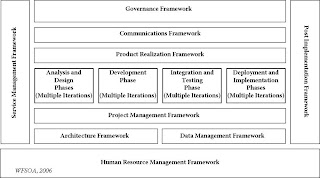
- Govern and Assure (Direct)
- Strategise and Plan (Direct)
- Operate and Optimise (Execute)
- Change and Transform (Execute)
The Val IT Framework (IT Governance Institute - ITGI)
COBIT Framweork for the management and delivery of high-quality IT-enabled services
Val IT / COBIT IT Governance Approach
Val IT
- Strategy (Are we doing the right things?)
- Value (Are we getting the benefits?)
COBIT
- Architecture (Are we doing them the right way?)
- Delivery (Are we executing them well?)
Value Governance Maturity
0 - Non-existent
1 - Initial
2 - Repeatable
3 - Defined
4 - Managed
5 - Optimised
*Business Case Best Practices
- Justification for an investment
- Communication on assumptions about costs and benefits
- Method to inform decision making on allocating scarce resources and capital
Business Case Key Issues
- Developing the Business Case
- Reasons for Project
- Options - Scenario Planning
- Benefit expected
- Risk
- Cost - Financial ROI, DCF NPV
- Timescale
- Investment Appraisal - Cost Benefit Analysis
- Evaluation
Templates
Approval Process and Gates
Acceptance Criteria
- Alignment with Strategy
- Rank, Priority and Opportunity Cost
- Feasibility, Causality, Risk Aversion
Delivery of Benefits
Questions to ask about a Business Case
Is this busine?
Is it the best business case if we were to rank them?
Can we measure the changes?
Is there really a cause/effect link between this business case and the value?
What is the business case doesn't go forward - what are the real consequences?
*Continuous Decision Improvement
Use the outcomes of previous decision-making experiences to improve future decisions and apply techniques to optimize those decisions.
Disciplines
- Predictive Analytics & EDM
- Decision Support
- Optimisation
- Knowledge Mangement
The CDI Cycle
- Communicate improved strategy and policy for decision-making
- Apply policty: make decisions
- Monitor and collect data for analysis
- Analyse & Develop: Learn from earlier decisions and outcomes
*Value Engineering
1. Outcome Planning
2. Function Modeling
3. Speculation & invertion
4. Idea Development
5. Idea Portfolio Building
6. Decision Approval
7. Implementation
Functionality Models
Produce New Procedure
Determine Procedural Options
Establish Procedure Scope (Allocate SME Resource)
Identify Required Technical Outcome
Benefits Definition
Identifying benefit types
Determing benefit certainty
Clear Benefit definition makes functional silo behaviour less easy, exposes negative competition, makes it harder for people to simply be self-interested
Two key elements:
- Defining benefits
- Mapping benefits
What is the investment rationale (How hard is the Benefit Definition)?
- Renewal (Easy)
- Process IOmprovement (Moderate)
- Experiments (Hard)
- Transformation (Hard)
Defining Benefit Types
- Profit
- Revenue
- Growth
- Share
- Costs
- Time
- Productivity
- Risks
- Customer Experience
- Image & Reputation
- People's Morale
- Securable
- Committed
- Anticipated
- Noticeable
- Start the sentence with an active verb that identifies the change (two words)
- Add any subject and conditions
More/Less, Increse/Reduced, Deliver/Eliminate, Greater/Fewer, Faster/Slower, Maximise/Minimise
Benefit Definition Checklist
- Beneficiary
- Description
- Dependencies and CSFs (Critical Success Factor)
- Direct/Indirect - SCAN
- Timing
- Type
- Measurement
- Responsibility
*Benefit Mapping
Benefit Management - Critical Success Factors
- Framing
- People
- Analysis
- Measurement
- Governance
A benefits map connects:
- what is done (ie invested in or consumes resources)
- Tangible changes in the business (that result form those activities)
- The end benefits it delivers (meaningful to the business as ROI)
Engaging Business Stake Holders
Benefits Mapping: Planning the Investment
Business Objectives
- Improve Cost Structure
- Increase Asset Utilization
- Enhance Customer Value
- Expand Revenue Opportunities
- Reduce Product Proce
- Improve Product Capability
- Reduce Time to Market
- Reduce Product Lead Time
- Improve Product Quality
Business Transformation (Change) Initiatives
- Concurrent Product Introduction Processes
- Increase Re-use of Legacy Product Info
- Increase use of Lessons Learned
IT Enablement Programmes
- Product Lifecycle Management (PLM)
- Knowledge Management System
- PLM for Engineering
Benefits Mapping: Planning Benefit Delivery
- Identify business change activities (Benefits Map)
- Validate for each BU
- Link to Programme Mgt controls (Milestones)
- Monitor as lead indicators of benefit erosion
- Apply corrective action
Benefits Mapping: Implementing Benefit Realization
Benefits Mapping: Delivering Benefit Certainty
Projects->Initiative/Enabler->Value Driver->Objective/Benefit->Strategic Objective
Process Steps
- Executive sponsorship and briefing
- Access to documentation / information on initiatives
- Access to objectives
- Develop logical structure - strategic objectives through to project
- Share a strawman
- Agree focus with Executive Sponsor: business results nore important than purity of mapping
- Ensure building a map that can be developed with quantification
- Stop when your client has achieved what they needed
Benefits Map: Tracking Benefit Realization
- Activities
- Results
- Enabling Outcomes
- Managed Benefits