Step 1: Verify the Installation of the SMTP Service
In Control Panel, open Add/Remove Programs, click Add/Remove Windows Components. Click the Internet Information Services (IIS) component, click Details, and then verify that the SMTP Service check box is selected.
If it is not selected, click to select it, click OK, and then follow the installation directions that are displayed.
Step 2: Configure the SMTP Service to Relay for Internal Domains
Depending on the scenario, it may be necessary to configure the SMTP service to relay inbound messages for your internal domains.
1. Click Start, point to Programs, click Administrative Tools, and then click Internet Services Manager.
2. Expand the tree under the server name, and then expand the Default SMTP Virtual Server. By default, you should have a Local (Default) domain with the fully qualified domain name of the server.
3. Configure the domain for inbound:
a. Right-click the Domains icon, click New, and then click Domain.
b. Click Remote, click Next, and then type the forwarder.yourcompany.com in the Name box. Click Finish.
Configure the domain for relay
1. In the properties for the domain that you just created, click to select the Allow the Incoming Mail to be Relayed to this Domain check box.
2. If this is being set up for a internal domain, you should specify the server that receives e-mail for the domain name by the IP address in the Route domain dialog box.
3. Click the forward all e-mail to smart host option, and then type the IP address of the server that is responsible for e-mail for that domain in square brackets.
Note: Typing the IP address of the server in brackets is necessary so that the server recognizes this is an IP address and not to attempt a DNS lookup.
Step 3: Specify the Hosts That You Want to Openly Relay to All Domains
Note:
Anyone can send to the domains that you specified in Step 2.
This step is for hosts, which are most likely your internal servers that would need to send to all domains on the Internet. It is not recommended to not have any restrictions because anyone can use your server as an open relay. It is recommended to only allow the minimum, necessary hosts to openly relay to all domains. To do so:
1. Open the properties of the Default SMTP Virtual Server.
2. On the Access tab, click Relay.
3. Click Only the list below, make sure the list is empty. Check the checkbox before “Allow all computers which successfully authenticate to relay, regardless of the list above”.
Showing posts with label ALL. Show all posts
Showing posts with label ALL. Show all posts
Thursday, March 26, 2009
Install and Configure the Oracle 10g ODBC driver on Windows 2003 Server
Verify MDAC version 2.8 (use comcheck.exe).
If less than 2.8, install MDAC 2.8 by using Windows 2003 Server CDs.
Run CC_Pkg.exe
Install it in E:\Program Files\CompChecker
Run Component Checker
Make sure MDAC has version 2.8 and up
Setup Oracle ODBC and Provider for OLE DB drivers. Install or update TNSNAMES.ORA in E:\Program Files\\Network\Admin folder.
Install Oracle Client including ODBC and Provider for OLEDB
Open 10g_win32_client.zip
A. Run Setup.exe.
B. Oracle Universal installer screen.
Name: OraClient10g_hisrep
Path: E:\Oracle\Product\10.1.0\Client_hisrep
Chose “Administrator” option
Click ‘Next”
1. At Welcome Screen
-Leave ‘Typical’ button unchecked.
2. Select Naming Methods screen.
- Select ‘Local Naming’ option and > to ‘Selected Naming’ side.
- Click ‘Next’
3. Service Name screen.
- Enter sidname: hisrep
- Click ‘Next’
4. Select Protocols screen.
- Select TCP
-Click ‘Next”
5. TCP/IP Protocol screen.
- Host Name: hisreppldb.iweb.gm.com
- Keep ‘Use standard prot number of 1521.
- Click ‘Next”
6. Test screen.
- Keep ‘Yes, perform a test checked.
- Click ‘Next’
7. Net Service Name screen.
- Net Service Name: hisrep
- Click ‘Next’
8. Connect Test/Logon screen.
- Username: Medgate_v60_app
- Password: medgate60
- Click ‘OK’
9. Another Net Service Name? screen.
- Leave ‘No’ checked.
- Click ‘Next”
10. Net Service configuration Done screen.
- Click ‘Next’
11. Naming Methods configuration Done screen.
- Click ‘Next’
12. Done ‘OracleNet Configuration Complete’ screen.
- Click ‘Finish’
13. End of Installation screen.
- Click ‘Exit’
- Do you Really want to exit? prompt
- Click ‘Yes’
Verify ODBC driver.
Create new DSN source.
Go to Start->Administrative Tools->Data Source (ODBC)
Click “System DSN” Tab
Click “Add” button
Select the driver: “Oracle in OraDB10g_xxx”
Click “Finish”
Configure the Oracle ODBC Driver:
Data source name = <your_data_source>
Description = Oracle database
TNS Service name = <your_service_name>
UserID = <user_id>
TEST the database connection by click “Test Connection” button
Make sure it can establish connection. The connection will be used for other install components.
If less than 2.8, install MDAC 2.8 by using Windows 2003 Server CDs.
Run CC_Pkg.exe
Install it in E:\Program Files\CompChecker
Run Component Checker
Make sure MDAC has version 2.8 and up
Setup Oracle ODBC and Provider for OLE DB drivers. Install or update TNSNAMES.ORA in E:\Program Files\
Install Oracle Client including ODBC and Provider for OLEDB
Open 10g_win32_client.zip
A. Run Setup.exe.
B. Oracle Universal installer screen.
Name: OraClient10g_hisrep
Path: E:\Oracle\Product\10.1.0\Client_hisrep
Chose “Administrator” option
Click ‘Next”
1. At Welcome Screen
-Leave ‘Typical’ button unchecked.
2. Select Naming Methods screen.
- Select ‘Local Naming’ option and > to ‘Selected Naming’ side.
- Click ‘Next’
3. Service Name screen.
- Enter sidname: hisrep
- Click ‘Next’
4. Select Protocols screen.
- Select TCP
-Click ‘Next”
5. TCP/IP Protocol screen.
- Host Name: hisreppldb.iweb.gm.com
- Keep ‘Use standard prot number of 1521.
- Click ‘Next”
6. Test screen.
- Keep ‘Yes, perform a test checked.
- Click ‘Next’
7. Net Service Name screen.
- Net Service Name: hisrep
- Click ‘Next’
8. Connect Test/Logon screen.
- Username: Medgate_v60_app
- Password: medgate60
- Click ‘OK’
9. Another Net Service Name? screen.
- Leave ‘No’ checked.
- Click ‘Next”
10. Net Service configuration Done screen.
- Click ‘Next’
11. Naming Methods configuration Done screen.
- Click ‘Next’
12. Done ‘OracleNet Configuration Complete’ screen.
- Click ‘Finish’
13. End of Installation screen.
- Click ‘Exit’
- Do you Really want to exit? prompt
- Click ‘Yes’
Verify ODBC driver.
Create new DSN source.
Go to Start->Administrative Tools->Data Source (ODBC)
Click “System DSN” Tab
Click “Add” button
Select the driver: “Oracle in OraDB10g_xxx”
Click “Finish”
Configure the Oracle ODBC Driver:
Data source name = <your_data_source>
Description = Oracle database
TNS Service name = <your_service_name>
UserID = <user_id>
TEST the database connection by click “Test Connection” button
Make sure it can establish connection. The connection will be used for other install components.
Turn on ASP support in IIS (Windows 2003 server)
Turn on ASP support in IIS Administration.
Open IIS Manager
- click Web Sites
- open
- Right click
- Select Properties
- Select Tab ‘Home Directory”
- Click ‘Configuration Button”
- Verify that .ASP and .ASPX are in ‘Application Extensions’ list. Otherwise add them.
- Click OK to close.
Open IIS Manager
- click Web Sites
- open
- Right click
- Select Properties
- Select Tab ‘Home Directory”
- Click ‘Configuration Button”
- Verify that .ASP and .ASPX are in ‘Application Extensions’ list. Otherwise add them.
- Click OK to close.
Configure SMTP on IIS (Windows 2003)
Step 1: Verify the Installation of the SMTP Service
In Control Panel, open Add/Remove Programs, click Add/Remove Windows Components. Click the Internet Information Services (IIS) component, click Details, and then verify that the SMTP Service check box is selected.
If it is not selected, click to select it, click OK, and then follow the installation directions that are displayed.
Step 2: Configure the SMTP Service to Relay for Internal Domains
Depending on the scenario, it may be necessary to configure the SMTP service to relay inbound messages for your internal domains.
Click Start, point to Programs, click Administrative Tools, and then click Internet Services Manager.
Expand the tree under the server name, and then expand the Default SMTP Virtual Server. By default, you should have a Local (Default) domain with the fully qualified domain name of the server.
Configure the domain for inbound:
Right-click the Domains icon, click New, and then click Domain.
Click Remote, click Next, and then type the forwarder.gm.com in the Name box. Click Finish.
Configure the domain for relay
In the properties for the domain that you just created, click to select the Allow the Incoming Mail to be Relayed to this Domain check box.
If this is being set up for a internal domain, you should specify the server that receives e-mail for the domain name by the IP address in the Route domain dialog box.
Click the forward all e-mail to smart host option, and then type the IP address of the server that is responsible for e-mail for that domain in square brackets. IP of forwarder.yourcompany.com is:
[168.208.12.12]
Note: Typing the IP address of the server in brackets is necessary so that the server recognizes this is an IP address and not to attempt a DNS lookup.
Click OK.
In Control Panel, open Add/Remove Programs, click Add/Remove Windows Components. Click the Internet Information Services (IIS) component, click Details, and then verify that the SMTP Service check box is selected.
If it is not selected, click to select it, click OK, and then follow the installation directions that are displayed.
Step 2: Configure the SMTP Service to Relay for Internal Domains
Depending on the scenario, it may be necessary to configure the SMTP service to relay inbound messages for your internal domains.
Click Start, point to Programs, click Administrative Tools, and then click Internet Services Manager.
Expand the tree under the server name, and then expand the Default SMTP Virtual Server. By default, you should have a Local (Default) domain with the fully qualified domain name of the server.
Configure the domain for inbound:
Right-click the Domains icon, click New, and then click Domain.
Click Remote, click Next, and then type the forwarder.gm.com in the Name box. Click Finish.
Configure the domain for relay
In the properties for the domain that you just created, click to select the Allow the Incoming Mail to be Relayed to this Domain check box.
If this is being set up for a internal domain, you should specify the server that receives e-mail for the domain name by the IP address in the Route domain dialog box.
Click the forward all e-mail to smart host option, and then type the IP address of the server that is responsible for e-mail for that domain in square brackets. IP of forwarder.yourcompany.com is:
[168.208.12.12]
Note: Typing the IP address of the server in brackets is necessary so that the server recognizes this is an IP address and not to attempt a DNS lookup.
Click OK.
Install SMTP service under Windows Server 2003
The version of Microsoft IIS that ships with Windows 2003 contains a service that you can use to deliver mail using SMTP. To install this SMTP service, perform the following steps:
1. Start the Control Panel Add/Remove Programs applet.
2. Click Add/Remove Windows Components.
3. After the Windows Components Wizard appears, select Applications Server and click Details.
4. Select Internet Information Services (IIS), then click Details.
5. Select SMTP Service, then click OK as this figure shows.
6. Continue to click OK to close all other dialog boxes until you're back at the Windows Components Wizard page, then click Next.
Windows 2003 will copy the files required for the SMTP service (you might be prompted to insert the installation CD-ROM) and configure the service. You can also install the SMTP service through the E-mail Services tool, which is a POP3 component that automatically installs SMTP. Windows 2003 configures the SMTP service to use a default server, and you can use the IIS Manager to modify the server settings.
Determine MDAC version
Determining which version of MDAC is installed on a computer at any given time presents certain difficulties because individual MDAC files may have been replaced by an errant installer, which complicates the situation. Component Checker is probably the most useful tool that is available for verifying MDAC installations. Component Checker is available for download from Data Access and Storage Developer Center MDAC Downloads.
Install and Use the Component Checker Tool
The most reliable way to determine which version of MDAC is installed is to compare the version number of each MDAC DLL file to a list of the DLL files that are shipped with each MDAC version. The Component Checker can help you to do this. It checks the files on the computer, compares them to a list from each version of MDAC, and reports the closest match.To install Component Checker, follow these steps:
1. Browse to the following Microsoft Web site:
http://www.microsoft.com/downloads/details.aspx?FamilyId=8F0A8DF6-4A21-4B43-BF53-14332EF092C9&displaylang=en (http://www.microsoft.com/downloads/details.aspx?FamilyId=8F0A8DF6-4A21-4B43-BF53-14332EF092C9&displaylang=en)
2. Click the link to download Component Checker. When you are prompted by the browser, save Cc.exe (a self-extracting executable file) to the desktop.
3. On the desktop, double-click Cc.exe; this extracts the Component Checker files and installs to the default location, C:\Comcheck.
To use Component Checker to check the MDAC version, follow these steps:
1. From the Start menu, click Run.
2. In the Open text box, type c:\comcheck\comcheck.exe and then click OK.
3. In the Component Checker - Choose Analysis Type dialog box, select Perform Analysis of your machine and automatically determine the release version, and then click OK.
4. The program attempts to identify the MDAC version on your computer by scanning all of the core MDAC files and registry settings. This process normally takes several minutes. When finished, you should receive the following message:
The MDAC version that is closest to the version on your computer is 'XXXX'.
5. Click OK.
6. A summary of the Component Checker scan appears. Note that the Dir, FileDescription, and FileSize errors can be safely ignored.
Check the Version Information Stored in the Registry
Although not the most reliable way to check the MDAC version, checking the registry for the version information is an easy way to double-check this information (if you are not experiencing any MDAC-related issues).The version information is found in the following key:
HKEY_LOCAL_MACHINE\Software\Microsoft\DataAccess\FullInstallVer
To check the registry, follow these steps:
1.On the Start menu, click Run.
2.In the Open text box, type regedit and then click OK; this starts Registry Editor.
3.In the Navigation pane, drill-down to the following path:
HKEY_LOCAL_MACHINE\Software\Microsoft\DataAccess
4.In the Details pane, look in the Name column for FullInstallVer and Version. Each of these keys will have corresponding version information in the Data column.
5.When finished, click Exit on the Registry menu to close Registry Editor.
1. Start the Control Panel Add/Remove Programs applet.
2. Click Add/Remove Windows Components.
3. After the Windows Components Wizard appears, select Applications Server and click Details.
4. Select Internet Information Services (IIS), then click Details.
5. Select SMTP Service, then click OK as this figure shows.
6. Continue to click OK to close all other dialog boxes until you're back at the Windows Components Wizard page, then click Next.
Windows 2003 will copy the files required for the SMTP service (you might be prompted to insert the installation CD-ROM) and configure the service. You can also install the SMTP service through the E-mail Services tool, which is a POP3 component that automatically installs SMTP. Windows 2003 configures the SMTP service to use a default server, and you can use the IIS Manager to modify the server settings.
Determine MDAC version
Determining which version of MDAC is installed on a computer at any given time presents certain difficulties because individual MDAC files may have been replaced by an errant installer, which complicates the situation. Component Checker is probably the most useful tool that is available for verifying MDAC installations. Component Checker is available for download from Data Access and Storage Developer Center MDAC Downloads.
Install and Use the Component Checker Tool
The most reliable way to determine which version of MDAC is installed is to compare the version number of each MDAC DLL file to a list of the DLL files that are shipped with each MDAC version. The Component Checker can help you to do this. It checks the files on the computer, compares them to a list from each version of MDAC, and reports the closest match.To install Component Checker, follow these steps:
1. Browse to the following Microsoft Web site:
http://www.microsoft.com/downloads/details.aspx?FamilyId=8F0A8DF6-4A21-4B43-BF53-14332EF092C9&displaylang=en (http://www.microsoft.com/downloads/details.aspx?FamilyId=8F0A8DF6-4A21-4B43-BF53-14332EF092C9&displaylang=en)
2. Click the link to download Component Checker. When you are prompted by the browser, save Cc.exe (a self-extracting executable file) to the desktop.
3. On the desktop, double-click Cc.exe; this extracts the Component Checker files and installs to the default location, C:\Comcheck.
To use Component Checker to check the MDAC version, follow these steps:
1. From the Start menu, click Run.
2. In the Open text box, type c:\comcheck\comcheck.exe and then click OK.
3. In the Component Checker - Choose Analysis Type dialog box, select Perform Analysis of your machine and automatically determine the release version, and then click OK.
4. The program attempts to identify the MDAC version on your computer by scanning all of the core MDAC files and registry settings. This process normally takes several minutes. When finished, you should receive the following message:
The MDAC version that is closest to the version on your computer is 'XXXX'.
5. Click OK.
6. A summary of the Component Checker scan appears. Note that the Dir, FileDescription, and FileSize errors can be safely ignored.
Check the Version Information Stored in the Registry
Although not the most reliable way to check the MDAC version, checking the registry for the version information is an easy way to double-check this information (if you are not experiencing any MDAC-related issues).The version information is found in the following key:
HKEY_LOCAL_MACHINE\Software\Microsoft\DataAccess\FullInstallVer
To check the registry, follow these steps:
1.On the Start menu, click Run.
2.In the Open text box, type regedit and then click OK; this starts Registry Editor.
3.In the Navigation pane, drill-down to the following path:
HKEY_LOCAL_MACHINE\Software\Microsoft\DataAccess
4.In the Details pane, look in the Name column for FullInstallVer and Version. Each of these keys will have corresponding version information in the Data column.
5.When finished, click Exit on the Registry menu to close Registry Editor.
Enterprise Master Data Management (MDM)
Introduction
•Goal: Single place where all common master data in an organization is stored and managed. The data would be accurate, consistent, and maintained in a coherent and secure manner.
•Provides a consistent understanding and trust of master data entities
•Provides mechanisms for consistent use of master data across the organization
•Is designed to accommodate and manage change
Why MDM
•Cross-LOB Perspective (Investments, Loans, Deposits; sees data as critical to operations, not see value in sharing)
•Cross-Channel Perspective (dist. Channel- Partner, Internet, Branch; different solutions->account-centric->customer centric))
•Cross-Business Subdomain Perspective (Case history, Contact preference, Party; different scope)
•Cross-Application/Technology Perspective (packaged apps; variance in technoical platform
•Mergers and Acquisitions
MDM System
•Master Data Domains – Recognition of CDI and PIM. Three primary domains: party, product and account
•Methods of Use – Collaborative Authoring (users & systems to reach agreement), Operational (providing stateless services), Analytical (trusted data source, key function or analytics)
•System of Record (read-only) vs. System of Reference
•Consistency of Data – Absolute Consistency (consistent all the time), Convergent Consistency
•Implementation Styles – Consolidation Implementation (gold source); Registry Implementation (for read-only); Coexistence Implementation (master in many locations); Transactional Hub Implementation.
•Categorizing Data – Metadata, Reference Data, Master Data, Transaction Data, Historical Data
Collaborative MDM (New Product Introduction example)
•1. Receive Notification of New Item
•2. Create Draft Item
•3. Classify Item and Assign SKU
•4. Define Item Properties
•5. Define Marketing Properties
•6. Assign Item to Locations
•7. Define Finance Properties
•8. Approve Product Definition
Operational MDM (OLTP)- New Account Opening
•1. RECORD Arrangement Request
•2. ANALYZE Customer RElationship
•3. ANALYZE Arrangement Request
- APPLY Product Policy
- APPLY Credit Rating Scale
- FORECAST Arrangement Risk
- OFFER Arrangement
Implementation Style
•Consolidation
•Registry
•Coexistence
•Transactional Hub
Data Category
•Metadata
•Reference data
•Master Data
•Transactional Data
•Historical Data
Business Benefits of MDM
•Consistent Understanding and Trust of Master Data Entities – Accuracy, Completeness, Consistency, Timeliness, Relevance, Trust
•Consistent Use of Master Data Across the Organization – Cost Savings and Efficiencies, Regulatory Compliance
•Accommodate and Manage Change – Reducing Time to Market, Revenue Enhancement and Other New Opportunities, Ability to Rapidly Innovate, Product or Service Innovation, Process Innovation, Market Innovation, Supply Chain Innovation, Accommodating Mergers and Acquisitions, Introduction of New Requirements
An SOA Enabler (SOA Architecture)
•Layer 1 – Consumers
•Layer 2 - Business Process (Composition, Choreography, Business State Machine, Orchestration)
•Layer 3 – Services (atomic and composite)
•Layer 4 – Service Components
•Layer 5 – Application Services
•Layer 6 – Data Repositories & Information Services
•Layer 7 – Integration (Enterprise Service Bus)
•Layer 8 – Quality of Service (Security, Management, Monitoring)
•Layer 9 - Governance
Characteristics of SOA services (also for MDM)
•Service reuse
•Service granularity
•Service modularity and loose coupling
•Service composability
•Service componentization and encapsulation
•Compliance with standards (both common and industry-specific)
•Services identification and categorization
•Provisioning and delivery
•Monitoring and tracking
Information as a Service: Characteristics
•Definition – The structure and the semantics of the information needs to be well defined and commonly available
•Quality – integrity of the data needs to be ensured for retrieval and update
•Governance – Changes to the service and the underlying information need to be governed in a uniform and consistent manner
MDM Reference Architecture
•Conceptual Level
•Logical Level
•Physical Level
Architecture Pattern
•Process-Focused Application Integration (integration of applications)
•Information-Focused Application Integration (synchronize master data among MDM hub and underlying legacy systems)
•MDM Hub Patterns (style of MDM deployment)
MDM Ref – Key Functional and Technical Capabilities
•Master Data Lifecycle Mgmt Capability – from created to no longer required; group and define hierarchies; flexible mapping; define master data hierarchies, relationships, groupings; versioning; model multiple taxonomies; authoring; security; audit;
•Data Quality Mgmt Capability – analysis & profiling; standardization, data validation, data cleansing logic; Data reconciliation; data governance; measure the staleness of data
•Master Data Harmonization Capabilities – Integration (messaging, service invocation, batch, ETL, FTP); error-handling; support high-volume transaction
•Analysis and Insight Capabilities – discover insightful relationships; improve business decision; access structured and unstructured information; manage the state of a process; configure event management services
Conceptual Architecture
•Framework to manage and maintain master data
•Scalable, highly available, adaptive architecture
•Coordinate, manage the lifecycle of master data across the enterprise
•Accurate critical business information available as a service
•Cleanse data, improve the quality and consistency of master data
•Make master data active by detecting events and generating operations to manage master data
•enable the ability to implement solutions
MDM Solution – Key architecture building blocks
•Third-Party Data Service Provider
•Process Manager to choreograph
•Connectivity and Interoperability Layer
•MDM Services and Master Data Repository
•Information Integration Services
•Identity Analytics
MDM Solution – Architecture Principles
•Provide ability to decouple information from app & process
•Available as a strategic asset for enterprise
•Authoritative source for master data (manage integrity, control distribution in a standardized way)
•On an architectural framework and reusable services
•Based on industry-accepted open computing standards
•Provide flexibility to accommodate changes
•Highest regard for preserving the ownership of data, integrity and security of data
•Ability to incrementally implement a MDM Solution
MDM – Logical Architecture Components
•Interface Services
•Lifecycle Management Services
•Hierarchy and Relationship Mgmt Services
•Master Data Mgmt Event Mgmt Services
•Authoring Services
•Data Quality Mgmt Services
•Base Services
•Master Data Repository
MDM – Information Risk Analysis
•Identifying the information assets
•Assigning value to each asset
•Identifying each asset’s vulnerabilities and associated threats
•Calculating the risk for the identified assets
•Evaluating different countermeasures in terms of costs and reduction of risk they provide
•Recommending the appropriate countermeasures
MDM – Security and Privacy: Types of IT Risks
•Operational risks – failures in business process; denial of service attack;
•Regulatory and Compliance risks – meet business processes; adequately protecting sensitive data
•Reputational Risks -
MDM – Information Risk Management
•Risk Analysis for MDM
•Security Control Selection and Implementation
MDM – Identifying MDM Assets
•Sources of master data
•Master data itself
•Consumers of master data
•Other related assets
MDM – Security Consideration
•Policy
•Confidentiality
•Integrity
•Identity
•Authentication
•Authorization
•Audit
•User Registry
•Identity provisioning
•Identity token
•Identity mapping
•Identity Propagation
•Reverse Proxy
MDM – Security Considerations
•Identity Propagation, Mapping & Provisioning – Business (Trust Mgmt, Identity and Access (Authorization) Mgmt); Technical (Identity & Authentication Service, Policy Mgmt)
•Authorization – Business (manage identities, roles and groups); Technical (standards-based to handle specifying, distributing & enforcing authorization policies.
•Audit – Business (comply with policies & reports illustrating how well relative to policies; Technical (audit events, real-time and post-processing events reporting
•Data Protection – Business (describe business object level how master data should be protected); Technical (encryption, SSL, WS-Security)
Logical SOA Security Architecture
•Business Security Services tier
•Security Policy Mgmt tier
•IT Security Service tier
Security Enablers
•Cryptography
•Key Management
•Hardware key Storage
•Cryptographic Hardware
•Malware Protection
•Isolation
•Firewalls
•Intrusion Detection
•Intrusion Prevention
•Time
•Security Event and Incident Mgmt (SEIM)
Policy Management
•Policy abstraction level
•Policy management lifecycle
•Policy Domains
Identity propagation
•Security Token Service (STS)
•SAML token for security token format
Authentication Services
•WS-Trust Security Token Service (STS)
Authorization Services
•Service Consumer
•MDM SOA Services Layer
•MDM Services Implementation
•Master Data Repositories
•Goal: Single place where all common master data in an organization is stored and managed. The data would be accurate, consistent, and maintained in a coherent and secure manner.
•Provides a consistent understanding and trust of master data entities
•Provides mechanisms for consistent use of master data across the organization
•Is designed to accommodate and manage change
Why MDM
•Cross-LOB Perspective (Investments, Loans, Deposits; sees data as critical to operations, not see value in sharing)
•Cross-Channel Perspective (dist. Channel- Partner, Internet, Branch; different solutions->account-centric->customer centric))
•Cross-Business Subdomain Perspective (Case history, Contact preference, Party; different scope)
•Cross-Application/Technology Perspective (packaged apps; variance in technoical platform
•Mergers and Acquisitions
MDM System
•Master Data Domains – Recognition of CDI and PIM. Three primary domains: party, product and account
•Methods of Use – Collaborative Authoring (users & systems to reach agreement), Operational (providing stateless services), Analytical (trusted data source, key function or analytics)
•System of Record (read-only) vs. System of Reference
•Consistency of Data – Absolute Consistency (consistent all the time), Convergent Consistency
•Implementation Styles – Consolidation Implementation (gold source); Registry Implementation (for read-only); Coexistence Implementation (master in many locations); Transactional Hub Implementation.
•Categorizing Data – Metadata, Reference Data, Master Data, Transaction Data, Historical Data
Collaborative MDM (New Product Introduction example)
•1. Receive Notification of New Item
•2. Create Draft Item
•3. Classify Item and Assign SKU
•4. Define Item Properties
•5. Define Marketing Properties
•6. Assign Item to Locations
•7. Define Finance Properties
•8. Approve Product Definition
Operational MDM (OLTP)- New Account Opening
•1. RECORD Arrangement Request
•2. ANALYZE Customer RElationship
•3. ANALYZE Arrangement Request
- APPLY Product Policy
- APPLY Credit Rating Scale
- FORECAST Arrangement Risk
- OFFER Arrangement
Implementation Style
•Consolidation
•Registry
•Coexistence
•Transactional Hub
Data Category
•Metadata
•Reference data
•Master Data
•Transactional Data
•Historical Data
Business Benefits of MDM
•Consistent Understanding and Trust of Master Data Entities – Accuracy, Completeness, Consistency, Timeliness, Relevance, Trust
•Consistent Use of Master Data Across the Organization – Cost Savings and Efficiencies, Regulatory Compliance
•Accommodate and Manage Change – Reducing Time to Market, Revenue Enhancement and Other New Opportunities, Ability to Rapidly Innovate, Product or Service Innovation, Process Innovation, Market Innovation, Supply Chain Innovation, Accommodating Mergers and Acquisitions, Introduction of New Requirements
An SOA Enabler (SOA Architecture)
•Layer 1 – Consumers
•Layer 2 - Business Process (Composition, Choreography, Business State Machine, Orchestration)
•Layer 3 – Services (atomic and composite)
•Layer 4 – Service Components
•Layer 5 – Application Services
•Layer 6 – Data Repositories & Information Services
•Layer 7 – Integration (Enterprise Service Bus)
•Layer 8 – Quality of Service (Security, Management, Monitoring)
•Layer 9 - Governance
Characteristics of SOA services (also for MDM)
•Service reuse
•Service granularity
•Service modularity and loose coupling
•Service composability
•Service componentization and encapsulation
•Compliance with standards (both common and industry-specific)
•Services identification and categorization
•Provisioning and delivery
•Monitoring and tracking
Information as a Service: Characteristics
•Definition – The structure and the semantics of the information needs to be well defined and commonly available
•Quality – integrity of the data needs to be ensured for retrieval and update
•Governance – Changes to the service and the underlying information need to be governed in a uniform and consistent manner
MDM Reference Architecture
•Conceptual Level
•Logical Level
•Physical Level
Architecture Pattern
•Process-Focused Application Integration (integration of applications)
•Information-Focused Application Integration (synchronize master data among MDM hub and underlying legacy systems)
•MDM Hub Patterns (style of MDM deployment)
MDM Ref – Key Functional and Technical Capabilities
•Master Data Lifecycle Mgmt Capability – from created to no longer required; group and define hierarchies; flexible mapping; define master data hierarchies, relationships, groupings; versioning; model multiple taxonomies; authoring; security; audit;
•Data Quality Mgmt Capability – analysis & profiling; standardization, data validation, data cleansing logic; Data reconciliation; data governance; measure the staleness of data
•Master Data Harmonization Capabilities – Integration (messaging, service invocation, batch, ETL, FTP); error-handling; support high-volume transaction
•Analysis and Insight Capabilities – discover insightful relationships; improve business decision; access structured and unstructured information; manage the state of a process; configure event management services
Conceptual Architecture
•Framework to manage and maintain master data
•Scalable, highly available, adaptive architecture
•Coordinate, manage the lifecycle of master data across the enterprise
•Accurate critical business information available as a service
•Cleanse data, improve the quality and consistency of master data
•Make master data active by detecting events and generating operations to manage master data
•enable the ability to implement solutions
MDM Solution – Key architecture building blocks
•Third-Party Data Service Provider
•Process Manager to choreograph
•Connectivity and Interoperability Layer
•MDM Services and Master Data Repository
•Information Integration Services
•Identity Analytics
MDM Solution – Architecture Principles
•Provide ability to decouple information from app & process
•Available as a strategic asset for enterprise
•Authoritative source for master data (manage integrity, control distribution in a standardized way)
•On an architectural framework and reusable services
•Based on industry-accepted open computing standards
•Provide flexibility to accommodate changes
•Highest regard for preserving the ownership of data, integrity and security of data
•Ability to incrementally implement a MDM Solution
MDM – Logical Architecture Components
•Interface Services
•Lifecycle Management Services
•Hierarchy and Relationship Mgmt Services
•Master Data Mgmt Event Mgmt Services
•Authoring Services
•Data Quality Mgmt Services
•Base Services
•Master Data Repository
MDM – Information Risk Analysis
•Identifying the information assets
•Assigning value to each asset
•Identifying each asset’s vulnerabilities and associated threats
•Calculating the risk for the identified assets
•Evaluating different countermeasures in terms of costs and reduction of risk they provide
•Recommending the appropriate countermeasures
MDM – Security and Privacy: Types of IT Risks
•Operational risks – failures in business process; denial of service attack;
•Regulatory and Compliance risks – meet business processes; adequately protecting sensitive data
•Reputational Risks -
MDM – Information Risk Management
•Risk Analysis for MDM
•Security Control Selection and Implementation
MDM – Identifying MDM Assets
•Sources of master data
•Master data itself
•Consumers of master data
•Other related assets
MDM – Security Consideration
•Policy
•Confidentiality
•Integrity
•Identity
•Authentication
•Authorization
•Audit
•User Registry
•Identity provisioning
•Identity token
•Identity mapping
•Identity Propagation
•Reverse Proxy
MDM – Security Considerations
•Identity Propagation, Mapping & Provisioning – Business (Trust Mgmt, Identity and Access (Authorization) Mgmt); Technical (Identity & Authentication Service, Policy Mgmt)
•Authorization – Business (manage identities, roles and groups); Technical (standards-based to handle specifying, distributing & enforcing authorization policies.
•Audit – Business (comply with policies & reports illustrating how well relative to policies; Technical (audit events, real-time and post-processing events reporting
•Data Protection – Business (describe business object level how master data should be protected); Technical (encryption, SSL, WS-Security)
Logical SOA Security Architecture
•Business Security Services tier
•Security Policy Mgmt tier
•IT Security Service tier
Security Enablers
•Cryptography
•Key Management
•Hardware key Storage
•Cryptographic Hardware
•Malware Protection
•Isolation
•Firewalls
•Intrusion Detection
•Intrusion Prevention
•Time
•Security Event and Incident Mgmt (SEIM)
Policy Management
•Policy abstraction level
•Policy management lifecycle
•Policy Domains
Identity propagation
•Security Token Service (STS)
•SAML token for security token format
Authentication Services
•WS-Trust Security Token Service (STS)
Authorization Services
•Service Consumer
•MDM SOA Services Layer
•MDM Services Implementation
•Master Data Repositories
Oracle 8.1.6 Recovery Manager (RMAN)
Overview
•Command-line and Enterprise Manager-based tool
•Optimize performance & space consumption
•Integrate with Oracle Secure Backup
•Free dependency on OS and SQL*Plus
Functional Components
•Target DB to be backed up
•RMAN client
•A flash recovery area (disk location)
Backup and restore on Windows (32bit)
•Run run_rman.bat (can be added to schedule tasks list)
•Log File (C:\Database_Migration\RMAN\ORCL81_.log
RMAN – Files
•Run_rman.bat – main batch script
•run_sql.txt: - sql script for backup controlfile to trace
•rman_cmf.txt: rman script for backup database and old archived logs
•run_bak_ctl.txt: sql script for backup controlfile
•restore_steps.txt:steps for restore whole database from backup files
Steps to run scripts
•Step1. delete old backup files.
•Step2. create controlfile trace file and then copy it to the backup folder
•Step3. rum rman backup scripts
•Step4. using winrar compress the backup files (if winrar is available)
Parameters to be modified
•paths in run_rman.bat, rman_cmf.txt, run_bak_ctl.txt
•NowDate, Month, Day definition in run_rman.bat according to your windows system.
•winrar in run_rman.bat. You may need add the path of winrar to system path or use absolute path
If Error ORA-19602 is encountered
•ORA-19602: cannot backup or copy active file in NOARCHIVELOG mode
•C:\>SVRMGRL
•SVRMGR>connect internal
•SVRMGR>shutdown immediate
•SVRMGR>startup (if error, try ‘mount’)
•SVRMGR>alter database archivelog;
•
•SVRMGR>startup
Recover database
•Launch CMD screen (db is mount)
•C:>set oracle_sid=GEMSDB81
•C:>sqlplus /nolog
•SQL>connect / as sysdba
•Command-line and Enterprise Manager-based tool
•Optimize performance & space consumption
•Integrate with Oracle Secure Backup
•Free dependency on OS and SQL*Plus
Functional Components
•Target DB to be backed up
•RMAN client
•A flash recovery area (disk location)
Backup and restore on Windows (32bit)
•Run run_rman.bat (can be added to schedule tasks list)
•Log File (C:\Database_Migration\RMAN\ORCL81_
RMAN – Files
•Run_rman.bat – main batch script
•run_sql.txt: - sql script for backup controlfile to trace
•rman_cmf.txt: rman script for backup database and old archived logs
•run_bak_ctl.txt: sql script for backup controlfile
•restore_steps.txt:steps for restore whole database from backup files
Steps to run scripts
•Step1. delete old backup files.
•Step2. create controlfile trace file and then copy it to the backup folder
•Step3. rum rman backup scripts
•Step4. using winrar compress the backup files (if winrar is available)
Parameters to be modified
•paths in run_rman.bat, rman_cmf.txt, run_bak_ctl.txt
•NowDate, Month, Day definition in run_rman.bat according to your windows system.
•winrar in run_rman.bat. You may need add the path of winrar to system path or use absolute path
If Error ORA-19602 is encountered
•ORA-19602: cannot backup or copy active file in NOARCHIVELOG mode
•C:\>SVRMGRL
•SVRMGR>connect internal
•SVRMGR>shutdown immediate
•SVRMGR>startup (if error, try ‘mount’)
•SVRMGR>alter database archivelog;
•
•SVRMGR>startup
Recover database
•Launch CMD screen (db is mount)
•C:>set oracle_sid=GEMSDB81
•C:>sqlplus /nolog
•SQL>connect / as sysdba
SOA for Business Developer
SOA for Business
•Open Standards
•Structure of a SOA Application – composed largely of services (Integration Services, Business Services, Data-Access Services)
•Web and Binary-Exchange Services – WSDL, SOAP, HTTP
•Presentation Services – Portlet, HTML,
•Runtime Products – security, service allocation, service composition, logging
•Loose Coupling
•Service Registry
•Service Level Agreements
Service Aspects
•Service Implementation - Logic
•Elementary access details – Location, binding, protocol, formatting
•Contract – interface and Quality of Service
Message Exchange Patterns
•One-way pattern – (fire-and-forget)
•Request-response pattern – (in-out)
•Notification pattern – (out-only)
•Solicit-response pattern – (out-in)
•Synchronous and Asynchronous Communication
•Callbacks – (Request and callback)
Quality of Service
•Reliability guarantees- availability, throughput, response time and probability, assured message
•Security mechanisms – Authentication, authorization, confidentiality, integrity, non-repudiation, attack protection
•Service coordination, including transaction control – Orchestration, Choreography
•Runtime update of address, binding, and message content – flow of traffic change, message reformat, send message to destination other than the requester
Process Steps
•Analyzing a Business Process
•Identifying Problems with current Process
•Communicating the Assumptions in Writing
•Isolating Services
•Creating the application
XML Schema
•Data Type – primitive, derived, simple, complex
•Purposes – data exchange, validation rules
•Groups, Sequencing,
SOA Standards
•WSDL
•SOAP
•UDDI
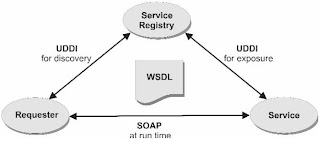
Introduction to BPEL
•BPEL process fulfills a workflow by accessing one service after another (partner service)
•BPEL activity is equivalent to a function call
•Running time can be far longer than other kinds of software
•Mechanisms for fault handling, compensation, correlation
•BPEL abstract process – subset of BPEL executable process (no implementation)
Additional language used by BPEL
•Query Language – XPath
•Expression language – XPath, Java
•doXslTransform
•Can use WSDL as source of data types
•PartnerLinkType (WSDL) – runtime conversation to partner service
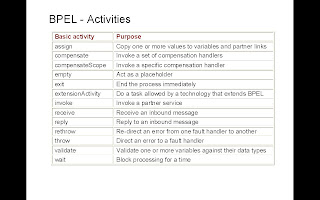
BPEL Basics
•Activities– assign,compensate,compensateScope, empty, exit, extensionActivity, invoke, receive, reply, rethrow, throw, validate, wait
• An XML-base language for creating a process
•1. Accept a request for an insurance quote
•2. If the submitted details are appropriate, calculate the quote and include it in the response
•3. Otherwise, say “No” and include a justfication

BPEL - Partner Links
•Give details on the relationship between the BPEL process and each partner service
<partnerlinks>
<partnerlink name="ProcessQuote" partnerlinktype="ProcessQuotePLT" myrole="ProcessQuoteRole">
<partnerlink name="mainframeQuoteMgr" partnerrole="partnerRole" partnerlinktype="PartnerLinkPLT">
</partnerlinks>
BPEL - Variables
•assigns variables, which are memory areas that are each described by a Web Services Description Language (WSDL) message but could have been described by an XML Schema element or type
<variables>
<variable name="quoteRequest" messageType="placeQuoteRequestMsg" />
<variable name="highlightQuote" messageType="placeQuoteResponseMsg" />
<variable name="buildQuoteReq" messageType="buildQuoteRequestMsg" />
<variable name="newHighlightQuote" messageType="buildQuoteResponseMsg" />
</variables>
BPEL - Quote Request
receives a quote request
<receive name="processQuoteRequest" createInstance="yes" operation="placeQuote" partnerLink="ProcessQuote"
portType="ProcessQuote" variable="quoteRequest">
</receive>
BPEL - Copy Data
uses XPath syntax to copy data from the received message to a variable that is used for invoking another service
<assign name="AssignQuoteReq"> <copy>
<from variable="quoteRequest" part="placeQuoteParameters"> <query>/quoteInformation</query> </from>
<to variable="buildQuoteReq" part="buildQuoteParameters"> <query>/customerQuoteInfo</query></to>
</copy> </assign>
BPEL - Other Service
•invokes the other service, which calculates and returns a quote
<invoke name="CalculateQuote" inputVariable="buildQuoteReq" operation="buildQuote" outputVariable="newHighlightQuote" partnerLink="mainframeQuoteMgr" portType="QuoteManagement" />
BPEL - Copy to response
copies the quote details to another variable and in this way formats the response message
<assign name="AssignQuoteRes"> <copy>
<from variable="newHighlightQuote" part="buildQuoteResult"> <query>/quote</query> </from>
<to variable="highlightQuote" part="placeQuoteResult" > <query>/quote</query> </to>
</copy> </assign>
BPEL - Reply
•replies to the invoker, which may have been a Web application or a service
<reply name="processQuoteResponse" operation="placeQuote" partnerLink="ProcessQuote" portType="ProcessQuote" variable="highlightQuote" />
BPEL – General activities
•Run in a preset sequence
•Run in a loop
•Run on condition that a Boolean expression evaluates to true
•Run immediately or wait for some period of time, even years
•Run in response to an event that occurs after the process starts (specifically, in response to an inbound message, a calendar date and clock time, or the passing of time)
•Run in an order that differs for different instances of the same process
BPEL – Processes
•BPEL executable process – a Web service and acts as the hub in a service orchestration
•Software that runs an executable process is called a BPEL engine
•BPEL abstract process – similar to BPEL executable process but includes a subset of the information. It is a description of business logic, it omits implementation details in most cases
BPEL – WSDL
•PartnerLinkType – specifies the roles between the BPEL process and a partner service. (BPEL, WSDL)
•Port Type – WSDL
•Operations – WSDL
•Data types – XSD
BPEL – WSDL-based constructs
•Properties and property aliases benefits
•Use same name to access the same data in differently structured variables
•Name’s position change doesn’t necessarily change the logic in BPEL process
•BPEL correlation set (constants). Help direct an inbound message to the correct instance of BPEL process
BPEL – Process Elements
<process>
<import> </import>
<partnerLinks> </partnerLinks>
<messageExchanges> </messageExchanges>
<variables> </variables>
<correlationSets> </correlationSets>
<faultHandlers> </faultHandlers>
<eventHandlers> </eventHandlers>
<!— The previous two elements include activities, as does the subsequent content of the process element. Activities can be enclosed in scopes, as described later. —>
</process>
BPEL – File Structure
•Import - provides access to a WSDL definition or an XML Schema
•Partner link - is a kind of specialized variable that describes the relationship between the BPEL process and a partner service
•Message exchange - is an idnetifier that is used to avoid an ambiguous case in a complex usiness scenario – specifically, to pair a BPEL activity that receives a message with the activity that issues a reply
•Variable - contains business data (message, process logic)
•Correlation set – listing of properties used to correlate service instances
•Fault handler – a set of activities that run in response to a fault (failure in the process)
•Event handler – a set of activities that run concurrently with other activities, in response either to the passage of time or to receipt of a message
BPEL – Partner Link
•myRole – enacted by the BPEL process
•Operations are described in port type that is related to the role.
•partnerRole – enacted by the partner service
•Multiple partner links can be based on the same partner link type.
BPEL – Correlation Sets
•Maintain data integrity
•A list of propertirs whose values are expected to remain constant throughout a process or throughout a specific scope
•Reference only in activities that receive or transmit data
•Inbound activity – BPEL engine to direct msg
•Outbound activity – verify property values
•Inboundor outbound – initiates the correlation set
BPEL – Fault Handling
•Purpose – minimize the effect of an error
•Composed of a catch or optional catchAll
•Each fault handler hasselection criteria, which include (optionally) the fault name and the type of data
•BPEL engine selects the fault handler whose selection criteria most closely mirror the fault
•If the fault has a name but no data, BPEL engine selects the fault handler whose selection criteria match exactly
•If no catchAll, BPEL provides default:
<catchAll>
<sequence>
<compensate/>
<rethrow/>
</sequence>
</catchAll>
BPEL – Compensation Handling
•Compensation for a successfully completed scope occurs under the guidance of a compensation handler
•Invocation always comes from a parent scope
•The compensateScope activity invodes the compensation handler of a specific nested scope
•A failure in scope A causes invocation of the compensation handler in scope B:
<scope name="A">
<compensationHandler>
<compensateScope target="B">
</compensationHandler>
<scope name="B">
<compensationHandler>
<!— a basic or structured activity is here —>
</compensationHandler>
</scope>
</scope>
BPEL – Termination Handling
•Set of activities that are issues when a running scope is being forced to terminate
•Default
<terminationHandler >
<compensate/>
</terminationHandler>
BPEL - Concurrency
Synchronized - Activities run concurrently and one activity is forced to wait for another
BPEL Activity – Start
•First activity (other than flow, scope or sequence)
•1. a receive activity
•2. a pick activity that contains only onMessage events
•Open Standards
•Structure of a SOA Application – composed largely of services (Integration Services, Business Services, Data-Access Services)
•Web and Binary-Exchange Services – WSDL, SOAP, HTTP
•Presentation Services – Portlet, HTML,
•Runtime Products – security, service allocation, service composition, logging
•Loose Coupling
•Service Registry
•Service Level Agreements
Service Aspects
•Service Implementation - Logic
•Elementary access details – Location, binding, protocol, formatting
•Contract – interface and Quality of Service
Message Exchange Patterns
•One-way pattern – (fire-and-forget)
•Request-response pattern – (in-out)
•Notification pattern – (out-only)
•Solicit-response pattern – (out-in)
•Synchronous and Asynchronous Communication
•Callbacks – (Request and callback)
Quality of Service
•Reliability guarantees- availability, throughput, response time and probability, assured message
•Security mechanisms – Authentication, authorization, confidentiality, integrity, non-repudiation, attack protection
•Service coordination, including transaction control – Orchestration, Choreography
•Runtime update of address, binding, and message content – flow of traffic change, message reformat, send message to destination other than the requester
Process Steps
•Analyzing a Business Process
•Identifying Problems with current Process
•Communicating the Assumptions in Writing
•Isolating Services
•Creating the application
XML Schema
•Data Type – primitive, derived, simple, complex
•Purposes – data exchange, validation rules
•Groups, Sequencing,
SOA Standards
•WSDL
•SOAP
•UDDI

Introduction to BPEL
•BPEL process fulfills a workflow by accessing one service after another (partner service)
•BPEL activity is equivalent to a function call
•Running time can be far longer than other kinds of software
•Mechanisms for fault handling, compensation, correlation
•BPEL abstract process – subset of BPEL executable process (no implementation)
Additional language used by BPEL
•Query Language – XPath
•Expression language – XPath, Java
•doXslTransform
•Can use WSDL as source of data types
•PartnerLinkType (WSDL) – runtime conversation to partner service
BPEL Basics
•Activities– assign,compensate,compensateScope, empty, exit, extensionActivity, invoke, receive, reply, rethrow, throw, validate, wait
• An XML-base language for creating a process
•1. Accept a request for an insurance quote
•2. If the submitted details are appropriate, calculate the quote and include it in the response
•3. Otherwise, say “No” and include a justfication

BPEL - Partner Links
•Give details on the relationship between the BPEL process and each partner service
<partnerlinks>
<partnerlink name="ProcessQuote" partnerlinktype="ProcessQuotePLT" myrole="ProcessQuoteRole">
<partnerlink name="mainframeQuoteMgr" partnerrole="partnerRole" partnerlinktype="PartnerLinkPLT">
</partnerlinks>
BPEL - Variables
•assigns variables, which are memory areas that are each described by a Web Services Description Language (WSDL) message but could have been described by an XML Schema element or type
<variables>
<variable name="quoteRequest" messageType="placeQuoteRequestMsg" />
<variable name="highlightQuote" messageType="placeQuoteResponseMsg" />
<variable name="buildQuoteReq" messageType="buildQuoteRequestMsg" />
<variable name="newHighlightQuote" messageType="buildQuoteResponseMsg" />
</variables>
BPEL - Quote Request
receives a quote request
<receive name="processQuoteRequest" createInstance="yes" operation="placeQuote" partnerLink="ProcessQuote"
portType="ProcessQuote" variable="quoteRequest">
</receive>
BPEL - Copy Data
uses XPath syntax to copy data from the received message to a variable that is used for invoking another service
<assign name="AssignQuoteReq"> <copy>
<from variable="quoteRequest" part="placeQuoteParameters"> <query>/quoteInformation</query> </from>
<to variable="buildQuoteReq" part="buildQuoteParameters"> <query>/customerQuoteInfo</query></to>
</copy> </assign>
BPEL - Other Service
•invokes the other service, which calculates and returns a quote
<invoke name="CalculateQuote" inputVariable="buildQuoteReq" operation="buildQuote" outputVariable="newHighlightQuote" partnerLink="mainframeQuoteMgr" portType="QuoteManagement" />
BPEL - Copy to response
copies the quote details to another variable and in this way formats the response message
<assign name="AssignQuoteRes"> <copy>
<from variable="newHighlightQuote" part="buildQuoteResult"> <query>/quote</query> </from>
<to variable="highlightQuote" part="placeQuoteResult" > <query>/quote</query> </to>
</copy> </assign>
BPEL - Reply
•replies to the invoker, which may have been a Web application or a service
<reply name="processQuoteResponse" operation="placeQuote" partnerLink="ProcessQuote" portType="ProcessQuote" variable="highlightQuote" />
BPEL – General activities
•Run in a preset sequence
•Run in a loop
•Run on condition that a Boolean expression evaluates to true
•Run immediately or wait for some period of time, even years
•Run in response to an event that occurs after the process starts (specifically, in response to an inbound message, a calendar date and clock time, or the passing of time)
•Run in an order that differs for different instances of the same process
BPEL – Processes
•BPEL executable process – a Web service and acts as the hub in a service orchestration
•Software that runs an executable process is called a BPEL engine
•BPEL abstract process – similar to BPEL executable process but includes a subset of the information. It is a description of business logic, it omits implementation details in most cases
BPEL – WSDL
•PartnerLinkType – specifies the roles between the BPEL process and a partner service. (BPEL, WSDL)
•Port Type – WSDL
•Operations – WSDL
•Data types – XSD
BPEL – WSDL-based constructs
•Properties and property aliases benefits
•Use same name to access the same data in differently structured variables
•Name’s position change doesn’t necessarily change the logic in BPEL process
•BPEL correlation set (constants). Help direct an inbound message to the correct instance of BPEL process
BPEL – Process Elements
<process>
<import> </import>
<partnerLinks> </partnerLinks>
<messageExchanges> </messageExchanges>
<variables> </variables>
<correlationSets> </correlationSets>
<faultHandlers> </faultHandlers>
<eventHandlers> </eventHandlers>
<!— The previous two elements include activities, as does the subsequent content of the process element. Activities can be enclosed in scopes, as described later. —>
</process>
BPEL – File Structure
•Import - provides access to a WSDL definition or an XML Schema
•Partner link - is a kind of specialized variable that describes the relationship between the BPEL process and a partner service
•Message exchange - is an idnetifier that is used to avoid an ambiguous case in a complex usiness scenario – specifically, to pair a BPEL activity that receives a message with the activity that issues a reply
•Variable - contains business data (message, process logic)
•Correlation set – listing of properties used to correlate service instances
•Fault handler – a set of activities that run in response to a fault (failure in the process)
•Event handler – a set of activities that run concurrently with other activities, in response either to the passage of time or to receipt of a message

BPEL – Partner Link
•myRole – enacted by the BPEL process
•Operations are described in port type that is related to the role.
•partnerRole – enacted by the partner service
•Multiple partner links can be based on the same partner link type.
BPEL – Correlation Sets
•Maintain data integrity
•A list of propertirs whose values are expected to remain constant throughout a process or throughout a specific scope
•Reference only in activities that receive or transmit data
•Inbound activity – BPEL engine to direct msg
•Outbound activity – verify property values
•Inboundor outbound – initiates the correlation set
BPEL – Fault Handling
•Purpose – minimize the effect of an error
•Composed of a catch or optional catchAll
•Each fault handler hasselection criteria, which include (optionally) the fault name and the type of data
•BPEL engine selects the fault handler whose selection criteria most closely mirror the fault
•If the fault has a name but no data, BPEL engine selects the fault handler whose selection criteria match exactly
•If no catchAll, BPEL provides default:
<catchAll>
<sequence>
<compensate/>
<rethrow/>
</sequence>
</catchAll>
BPEL – Compensation Handling
•Compensation for a successfully completed scope occurs under the guidance of a compensation handler
•Invocation always comes from a parent scope
•The compensateScope activity invodes the compensation handler of a specific nested scope
•A failure in scope A causes invocation of the compensation handler in scope B:
<scope name="A">
<compensationHandler>
<compensateScope target="B">
</compensationHandler>
<scope name="B">
<compensationHandler>
<!— a basic or structured activity is here —>
</compensationHandler>
</scope>
</scope>
BPEL – Termination Handling
•Set of activities that are issues when a running scope is being forced to terminate
•Default
<terminationHandler >
<compensate/>
</terminationHandler>
BPEL - Concurrency
Synchronized - Activities run concurrently and one activity is forced to wait for another
BPEL Activity – Start
•First activity (other than flow, scope or sequence)
•1. a receive activity
•2. a pick activity that contains only onMessage events
Oracle Application Server 10g Corporate Portal
Overview
•Browser-based environment for building, deploying, and maintaining enterprise portals
•Secure and manageable framework
•Organized and personalized views
•Self-service Web publishing
•Manageable deployment architecture
Oracle Application Server Components
•Oracle Internet Directory (OID)
•OracleAS Portal (OC4J)
•OracleAS Wireless
•OracleAS Web Cache
•OracleAS Personalization
•OracleAS Integration
•Browser-based environment for building, deploying, and maintaining enterprise portals
•Secure and manageable framework
•Organized and personalized views
•Self-service Web publishing
•Manageable deployment architecture
Oracle Application Server Components
•Oracle Internet Directory (OID)
•OracleAS Portal (OC4J)
•OracleAS Wireless
•OracleAS Web Cache
•OracleAS Personalization
•OracleAS Integration
Grid Computing
Architecture that pools large numbers of servers and storage into a less expensive, flexible, on-demand computing resource for all enterprise needs
- Standardize low cost components
- Consolidate shared resources
- Automate management operations
OracleAS 10g portal Solution
•Content management (Classify content, Navigate and access content; Route content for review and approval)
•Content display (Create, organize, and manage pages; Build and customize dynamic portlets
•Content integration (integrate applications and disparate data by using built-in functionality, including Web Clipplig, OmmiPortlet, and Portlet Builder
Major User Roles in OracleAS Portal
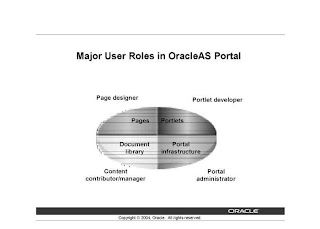
- Page designers
- Content contributors and content managers
- Portlet developers
- Portlet developers
•Page group – Root page; Subpages
•View mode; Graphical mode; Layout mode; List mode
Adding Content to Portal
Item
•An item is a basic unit of content on a portal page.
•Two kinds –
•Content item type
•Navigation item type
Content item types
•File and Simple File
•Simple Image
•Image and Simple Image Map
•PL/SQL and Simple PL/SQL
•Prge Link and Simple Page Link
•Text and Simple Text
•URL and Simple URL
•Zip File
Item-Related Features
•Versioning
•Item-level security
•Document control
•Publishing dates
•Expiry dates
•Approvals
•View mode; Graphical mode; Layout mode; List mode
Adding Content to Portal
Item
•An item is a basic unit of content on a portal page.
•Two kinds –
•Content item type
•Navigation item type
Content item types
•File and Simple File
•Simple Image
•Image and Simple Image Map
•PL/SQL and Simple PL/SQL
•Prge Link and Simple Page Link
•Text and Simple Text
•URL and Simple URL
•Zip File
Item-Related Features
•Versioning
•Item-level security
•Document control
•Publishing dates
•Expiry dates
•Approvals
Adding Items
With a WebDAV client, you can:
- Move content, files, and folders between your desktop and the document library
- Open, edit, and save file type items "in place" by using desktop application
Content Metadata
•Data about the content in the document library
•Set explicitly or implicitly
•Made up of three main components (Attributes; Categories; Perspectives)
Classifying Content in OracleAS Portal
•Category – A predefined attribute that is used to group or classify pages, items, and portlets
•Data about the content in the document library
•Set explicitly or implicitly
•Made up of three main components (Attributes; Categories; Perspectives)
Classifying Content in OracleAS Portal
•Category – A predefined attribute that is used to group or classify pages, items, and portlets
Creating Category
- Further classify content across categories
- Enable users to view related content classified in different categories
Creating Perspectives
Custom Types
•Custom types are unique types you create to extende the standard type definitions provided by OracleAS Protal.
•Custom attributes – User-defined attributes based on predefined data types created to store additional info about an item. (used in definition of custom item types and page types)
•Custom item types
•Custom page types
•[Item Type]n-n[Attribute]n-n[page type]
•Custom types are unique types you create to extende the standard type definitions provided by OracleAS Protal.
•Custom attributes – User-defined attributes based on predefined data types created to store additional info about an item. (used in definition of custom item types and page types)
•Custom item types
•Custom page types
•[Item Type]n-n[Attribute]n-n[page type]
Creating Custom Item Types
A Series of one or more approval routing steps
- Each step must have one or more approvers
- Routing to approvers can be in serial or in parallel
•OracleAS Protal object that contains portlets and items.
•A portal page is the face of the portal – that which the user interacts with to access informatipn and applications. The layout of a portal page is defined through regions
•A portal page combines the features of a directory folder and a browser page.Like a folder, a page can exist within a hierarchy of pages and can contain content.
Page Group
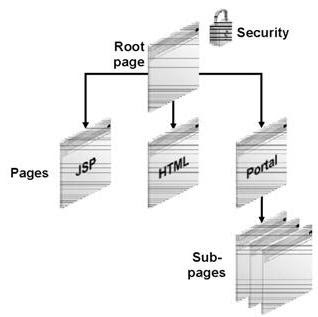
•A portal page is the face of the portal – that which the user interacts with to access informatipn and applications. The layout of a portal page is defined through regions
•A portal page combines the features of a directory folder and a browser page.Like a folder, a page can exist within a hierarchy of pages and can contain content.
Page Group

•A page group is a hierarchical collection of pages for which common attributes and mechanisms can be established to govern the behavior of the pages it contains.
•Consider – (Administering page groups; Managing content metadata; managing content presentation; Copying and moving content)
•Region – rectanglar area on a page used to define the page layout (Types: Item; Portlet; Sub-Page Links; Undefined)
Shared Objects
•Consider – (Administering page groups; Managing content metadata; managing content presentation; Copying and moving content)
•Region – rectanglar area on a page used to define the page layout (Types: Item; Portlet; Sub-Page Links; Undefined)
Shared Objects

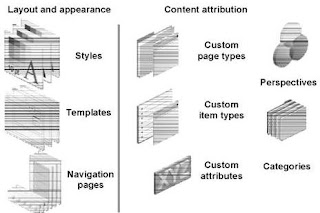
•Layout and appearance (Styles; Templates; Navigation pages)
•Content attribution (Custom page types; Custom item types; Custom attributes; Perspectives; Categories
Style
•Content attribution (Custom page types; Custom item types; Custom attributes; Perspectives; Categories
Style

•Set of values and parameters that controls the colors and fonts that are used by pages and regions within a page
Page template
•An object that enforces an standard layout and appearance for multiple pages
Page template
•An object that enforces an standard layout and appearance for multiple pages
Navigation Items
•Portal Smart Link
•Login/Logout Link
•Basic Search Box
•List of Objects
•Portal Smart Text
•Object Map Link
•Page Path
•Page Function
Page parameters
•Synchronize portlets residing on a page
•Enable the reuse of portlets on multiple pages with no additional coding
•Provide users the means to customize pages based on their input values
Portlet parameters
•Enable the portlet developer to declare a public data input interface for the page designer to use
•Give the page designer control over the input data to the portlet
Integrating Page and Portlet Parameters
Controlling Access to Page Groups
Controlling Access to Pages
•Manage
•Edit
•View
Accessing Portal Objects by Using Direct Access URLs
Web Clippling
A piece of existing Web content that can be repurposed in other Web pages, particularly portals.
OmniPortlet
A feature of Oracle AS Portal that enables you to quickly and easily publish data from various data sources and render the result in a variety of formats.
Supported data sources
•Spreadsheet
•SQL
•XML
•Web Service
•Web Page
Supported Data formates
•Tabular
•Chart
•News layout
•Bulleted list
•Form
Data-Driven Portlets (DB, SQL etc)
OracleAS Portal Forms
•Forms based on tables and views
•Master-detail forms based on two tables or views
•Forms based on stored procedures
OracleAS Poprtal Reports
Publishing Business Intelligence on a Portal Page
OrcleAS Discoverer provides two types of portlets
•List of Database Workbooks portlet: Contains the names and links to Discoverer workbooks
•Worksheets portlet: Enables you to place actual worksheetcontent on the portal page
Privileges
- Global privileges
- Objectr-level Privileges- The corresponding global privilege overrides an object-level privilege
Labels:
.ALL.,
ALL,
Architecture,
Business Objects,
EAI,
Enterprise Software,
Oracle
Service Oriented Enterprise (SOA)
Technical Foundation
1. ESB
2. Organizational Commitment to BPM
3. Enterprise Performance Management (EPM)
Three essential layers
1. Enterprise performance layer
2. Business process management layer
3. Service Oriented Architecture infrastructure
EPM - Focuses on specifying the strategic key performance indicators of the service enterprise and typing these to underlying business processes and policies
BPM – Utilize the infrastructure services provided b y service oriented architecture
ESB – Provides a common standards services-based brokering container
BPM
- Bring IT and businesses together and narrow, and sometimes eliminate, the IT-business divide.
- Allow enterprises to separate business processes and business rules to model and to manage them independently of applications
Three layers of service oriented enterprises
- Service Performance (Enterprise Performance Management)
- Service Integration (Business Process Management)
- IT Service Infrastructure (Service Oriented Architecture)
- Process-Oriented Culture (In service oriented enterprises products are processes)
What are strategies?
- Mission: A concise statement of the organization’s reason for existing
- Objectives: Broad statements describing the targeted direction
- Goals: Quantifications of objectives for a designated period of time
- Strategies: Statements of how objectives will be achieved and the major methods to be used
- Tactics: Specific action steps that map out how each strategy will be implemented
- KPIs: Measures of performance that show progress of each tactic in reaching the goals
Three Phases of SOEs
Phase 1: Point-to-point Enterprise Integration Focused (WSDL + SOAP)
Phase 2: Orchestration ESB, BPMS, Public Service Interface, Initial OoS Focus: WS-Security and Reliability, Initial Service Mgmt, Robust UDDI Deployments
Phase 3: Federated ESBs/BPMSs, Performance Mgmt of Service Application, End ot End Service Integration, B2B Process, Dynamic Discovery and Binding, Software as Service
Process Standardization
Notation – UML: OMG; BPMN: OMG
Process Definition / Execution – BPEL: OASIS; XPDL: WfMC; WS-CDL: W3C; ebXML BPSS; RosettaNet RNIF
Process Engine / Interoperability – Wf-XML: WfMC; BPSI: OMG
Business Process Management – Business process activity monitoring and performance capabilities
Business Performance Management- addition include monitoring and analysis of applications (BP, ERP, CRM, ect)
1. ESB
2. Organizational Commitment to BPM
3. Enterprise Performance Management (EPM)
Three essential layers
1. Enterprise performance layer
2. Business process management layer
3. Service Oriented Architecture infrastructure
EPM - Focuses on specifying the strategic key performance indicators of the service enterprise and typing these to underlying business processes and policies
BPM – Utilize the infrastructure services provided b y service oriented architecture
ESB – Provides a common standards services-based brokering container
BPM
- Bring IT and businesses together and narrow, and sometimes eliminate, the IT-business divide.
- Allow enterprises to separate business processes and business rules to model and to manage them independently of applications
Three layers of service oriented enterprises
- Service Performance (Enterprise Performance Management)
- Service Integration (Business Process Management)
- IT Service Infrastructure (Service Oriented Architecture)
- Process-Oriented Culture (In service oriented enterprises products are processes)
What are strategies?
- Mission: A concise statement of the organization’s reason for existing
- Objectives: Broad statements describing the targeted direction
- Goals: Quantifications of objectives for a designated period of time
- Strategies: Statements of how objectives will be achieved and the major methods to be used
- Tactics: Specific action steps that map out how each strategy will be implemented
- KPIs: Measures of performance that show progress of each tactic in reaching the goals
Three Phases of SOEs
Phase 1: Point-to-point Enterprise Integration Focused (WSDL + SOAP)
Phase 2: Orchestration ESB, BPMS, Public Service Interface, Initial OoS Focus: WS-Security and Reliability, Initial Service Mgmt, Robust UDDI Deployments
Phase 3: Federated ESBs/BPMSs, Performance Mgmt of Service Application, End ot End Service Integration, B2B Process, Dynamic Discovery and Binding, Software as Service
Process Standardization
Notation – UML: OMG; BPMN: OMG
Process Definition / Execution – BPEL: OASIS; XPDL: WfMC; WS-CDL: W3C; ebXML BPSS; RosettaNet RNIF
Process Engine / Interoperability – Wf-XML: WfMC; BPSI: OMG
Business Process Management – Business process activity monitoring and performance capabilities
Business Performance Management- addition include monitoring and analysis of applications (BP, ERP, CRM, ect)
Wednesday, March 25, 2009
WS-BPEL 2.0
•WS-BPEL: XML based programming language to describe high level business processes
•Web Service: using Web Service Description Language (WSDL)
BPEL Servers and Engine
•Create on demand
•BPEL engine: Focus to act as an execution engine which can be programmed using BPEL
BPEL Programming Language
•Programming logic – BPEL
•Data Types – XSD (XML Schema Definition)
•Input/Output (I/O) – WSDL (Web Services Description Language)
http://schemas.xmlsoap.org/ws/2003/03/business-process/" xmlns:print="http://www.eclipse.org/wsws/choreography/2004/engine/Print">
http://schemas.xmlsoap.org/wsdl/" location="../../test_bucket/service_libraries/wsws_EnginePrinterPort.wsdl" namespace="http://www.eclipse.org/wsws/choreography/2004/engine/Print" /> Hello World $hello_world.value
Importing WSDL and XSD files
•The 'import' statement in BPEL is a directive to import a WSDL or XSD file. Importing XSD files allows commonly used datatypes or datatypes required for a particular endpoint (thing that you speak to) to be defined in a file separate to the BPEL file. Importing WSDL files allows endpoint descriptions (definitions of things that you speak to) to be defined in files separate to the BPEL file.
Partner Link
•Partner Links can be thought of as placeholders for things that you actually speak to. A web service is described in full by the WSDL files that specify it but Partner Links allow you to have something like an instance of the web service that you speak to. A partner link basically maps to a WSDL web service 'portType', so one partnerLink (e.g. 'printService' above) maps to a single web service.
•However, partner links don't just describe what you speak to, they also can describe how other web service clients speak to you. In the partner link definition above, a 'partnerRole' attribute defines the web service that this BPEL process will speak to. Alternatively, the partner link could have a 'myRole' attribute which would define a web service that this BPEL process implements.
Variable definition
•Variables are used to contain data in BPEL. A variable can either contain an XSD value or a WSDL message. In the example above, a variable called 'hello_world' is declared as a container for WSDL messages of type 'print:PrintMessage'. Instead of the 'messageType' attribute, the variable could have had a 'type' attribute which would specify some xsd simple or complex type like 'xsd:string' or 'xsd:integer'.
•Variables are used to pass data in and out of web service endpoints.
Variable assignment
•Variables are manipulated in BPEL either through use via web service endpoints or by assignment. The example above shows a literal string value being assigned into the variable 'hello_world'. The variable 'hello_world' in this case is a WSDL message with a part called 'value'. The part called 'value' is an 'xsd:string' type. It can therefore have other 'xsd:string's assigned into it, including literal strings.
•The '$varname' syntax used to reference the variable here is standard XPATH expression syntax. The '.' separator is used to specify the WSDL message part. If the variable or the part were an XSD complex type then a '/' separator could be used to specify the sub-element within the complex type (e.g. '$hello_world.value/subvalue').
Web Service Invocation
•The 'invoke' activity in BPEL invokes a web service endpoint. This is where the BPEL process passes the 'Hello World' data (stored in the 'hello_world' variable) to the 'print' web service. The specified partnerLink tells the BPEL engine the address of the web service you want to invoke here. The 'print' operation specifies what you actually want the web service to do and the 'inputVariable' specifies that the input WSDL message should come from the 'hello_world' variable.
•What the web service actually does and exactly how the web service is implemented is not referenced in BPEL at all - all the implementation and definition information is contained within the defining WSDL file.
Web Service (in Java) - WSDL
http://schemas.xmlsoap.org/wsdl/" targetNamespace="http://www.eclipse.org/wsws/choreography/2004/engine/Print" xmlns:tns="http://www.eclipse.org/wsws/choreography/2004/engine/Print" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/" xmlns:format="http://schemas.xmlsoap.org/wsdl/formatbinding/" xmlns:java="http://schemas.xmlsoap.org/wsdl/java/" >
WSDL Messages
•WSDL messages are used to specify what the containers should be like that hold data when a WSDL operation is invoked. They are essentially lists of parts, each of which is an XSD simple or complex type.
•In the example above the 'PrintMessage' is defined as having a single part 'value', which is of type 'xsd:string'.
WSDL Port Types
•WSDL Port Types represent the definition of the web service itself. They describe the API or interface to the web service. A port type is a list of operations with 'input's and 'output's. Each of the 'input's and 'output's is a WSDL message that must have been previously defined (although it could have been imported from another WSDL file).
•A WSDL port type operation can also have any number of 'fault' elements. Each of these specifies an error message which would be an alternative to the 'output' message.
•Note that the name specified on the port type does not have any namespace prefix. This is because the port type is being defined here and now and it will inherit the target namespace. The 'printMessage' specified in the operation definition however DOES have a namespace prefix. This is because the printMessage has previously been defined and is being referenced. The 'tns:' prefix maps to the same namespace as the target namespace in the previously defined 'printMessage' message.
WSDL Port Type Bindings
•A 'binding' in WSDL specifies how the web service is actually implemented. Everything up until this point has been abstract and has dealt with only how to speak to the web service. The binding specifies what is on the other side that you are speaking to.
•A web service can be bound in many different ways. The most common bindings for a web service are: oas a SOAP/HTTP web service - whereby some implementation would be listening on a specified port and would accept SOAP messages over an HTTP transport. oas a Java web service - whereby some java class is mapped to the port type and is used directly as an implementation.
•In the binding above, a mapping has been created which specifies that the port type operation 'print' should be mapped to a Java method called 'print'. In addition to this, the XSD type 'string' has been mapped to the Java type 'String'.
•Using this mapping information a Java class can be specified later in the WSDL file as the 'address' of a concrete web service implementation. This class can be instantiated and when calls are made to the 'print' operation, they will be proxied to the 'print' method of this class. In the process of proxying the 'print' operation, any XSD strings will also be converted to Java strings as specified in the binding.
WSDL Service
•The WSDL 'service' element specifies a WSDL 'port'. A single port is an instance of a web service, which is implemented via a particular binding and which is available at a given address.
•In the case of our printout port, we are defining a web service which is bound using the previously defined Java binding and which can be found at the address 'org.eclipse...EnginePrinterPort‘.
•Note that the address is binding specific. The Java binding knows to interpret the 'className' attribute as a fully qualified Java class name and understands how to instantiate the class and proxy the WSDL operations to the Java methods specified in the 'binding' element.
Partner Link Types
•Partner Link Types are actually not a WSDL construct, but a BPEL construct. WSDL was around before BPEL and is purely designed towards describing web services. BPEL however requires that a partner link instance be associated with a particular WSDL port type. In this case there is only one end of the partner link which needs to be implemented - the 'printService' role. It is possible to have two roles in a single partner link type, each of which can be implemented by two communicating web services.
•The BPEL partnerLink definition specified a partner link type for the partner link and also either a 'myRole' or a 'partnerRole'. In our previous example the 'partnerRole' was defined as 'printService'. This is because the BPEL process will be speaking TO the 'printService', rather than acting as a 'printService' which other web clients can speak to (in that case the 'myRole' part of the partner link would have been defined).
Java Web Service Implementation
package org.eclipse.wsws.choreography.jengine.internal.extensions.wsdlbinding.wsif.ports; public class EnginePrinterPort { public void print(String s) { System.out.println(s); } }
The Java class specified in the WSDL 'service' element is the Java class that the BPEL engine will expect to find at runtime. We therefore need to create that java class and fill it with any methods that we specified mappings to in the WSDL 'binding' element (e.g. the 'print' method).
Deploying web service
•Once you have your BPEL file using the WSDL web service description you created and you have your compiled Java class that implements the web service you need to put it all together.
•The quickest and easiest way to do this is to use the 'Dependencies' tab in the Choreography launch configuration.
•Set up a launch configuration to run your Hello World BPEL file and then click on the 'Dependencies' tab. In here you can tell the engine which JARs are required for any user-provided java endpoints. Just click 'Add' and then choose the JAR containing your Hello World Java web service implementation. You should see the JAR show up in the table and you should ensure that the JAR is set to 'enabled'.
•Once you've added the dependency, just run the launch configuration. If you're running a distributed engine the engine will automatically pass the dependency JAR around for use on remote engines (engines on other host machines).
Redistributable Java Endpoint Deployment (Deploying as an Eclipse Plugin)
•If you want to write a Java web service implementation or build up a library of useful services that you want to be able to distribute or send to other people then you can expose dependencies via the Eclipse Extension Point mechanism.
•Just extend the extension point 'org.eclipse.wsws.choreography.internal_WSDLPortDependency' and add a reference to your JAR. The 'namespace' attributes specify which namespaces your JAR is required for. If any of the specified namespaces are used your JAR will be passed round the engine in anticipation of use by the BPEL program.
http://www.eclipse.org/wsws/choreography/2004/engine" />
•Web Service: using Web Service Description Language (WSDL)
BPEL Servers and Engine
•Create on demand
•BPEL engine: Focus to act as an execution engine which can be programmed using BPEL
BPEL Programming Language
•Programming logic – BPEL
•Data Types – XSD (XML Schema Definition)
•Input/Output (I/O) – WSDL (Web Services Description Language)
http://schemas.xmlsoap.org/ws/2003/03/business-process/" xmlns:print="http://www.eclipse.org/wsws/choreography/2004/engine/Print">
http://schemas.xmlsoap.org/wsdl/" location="../../test_bucket/service_libraries/wsws_EnginePrinterPort.wsdl" namespace="http://www.eclipse.org/wsws/choreography/2004/engine/Print" />
Importing WSDL and XSD files
•The 'import' statement in BPEL is a directive to import a WSDL or XSD file. Importing XSD files allows commonly used datatypes or datatypes required for a particular endpoint (thing that you speak to) to be defined in a file separate to the BPEL file. Importing WSDL files allows endpoint descriptions (definitions of things that you speak to) to be defined in files separate to the BPEL file.
Partner Link
•Partner Links can be thought of as placeholders for things that you actually speak to. A web service is described in full by the WSDL files that specify it but Partner Links allow you to have something like an instance of the web service that you speak to. A partner link basically maps to a WSDL web service 'portType', so one partnerLink (e.g. 'printService' above) maps to a single web service.
•However, partner links don't just describe what you speak to, they also can describe how other web service clients speak to you. In the partner link definition above, a 'partnerRole' attribute defines the web service that this BPEL process will speak to. Alternatively, the partner link could have a 'myRole' attribute which would define a web service that this BPEL process implements.
Variable definition
•Variables are used to contain data in BPEL. A variable can either contain an XSD value or a WSDL message. In the example above, a variable called 'hello_world' is declared as a container for WSDL messages of type 'print:PrintMessage'. Instead of the 'messageType' attribute, the variable could have had a 'type' attribute which would specify some xsd simple or complex type like 'xsd:string' or 'xsd:integer'.
•Variables are used to pass data in and out of web service endpoints.
Variable assignment
•Variables are manipulated in BPEL either through use via web service endpoints or by assignment. The example above shows a literal string value being assigned into the variable 'hello_world'. The variable 'hello_world' in this case is a WSDL message with a part called 'value'. The part called 'value' is an 'xsd:string' type. It can therefore have other 'xsd:string's assigned into it, including literal strings.
•The '$varname' syntax used to reference the variable here is standard XPATH expression syntax. The '.' separator is used to specify the WSDL message part. If the variable or the part were an XSD complex type then a '/' separator could be used to specify the sub-element within the complex type (e.g. '$hello_world.value/subvalue').
Web Service Invocation
•The 'invoke' activity in BPEL invokes a web service endpoint. This is where the BPEL process passes the 'Hello World' data (stored in the 'hello_world' variable) to the 'print' web service. The specified partnerLink tells the BPEL engine the address of the web service you want to invoke here. The 'print' operation specifies what you actually want the web service to do and the 'inputVariable' specifies that the input WSDL message should come from the 'hello_world' variable.
•What the web service actually does and exactly how the web service is implemented is not referenced in BPEL at all - all the implementation and definition information is contained within the defining WSDL file.
Web Service (in Java) - WSDL
http://schemas.xmlsoap.org/wsdl/" targetNamespace="http://www.eclipse.org/wsws/choreography/2004/engine/Print" xmlns:tns="http://www.eclipse.org/wsws/choreography/2004/engine/Print" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:wsdl="http://schemas.xmlsoap.org/wsdl/" xmlns:format="http://schemas.xmlsoap.org/wsdl/formatbinding/" xmlns:java="http://schemas.xmlsoap.org/wsdl/java/" >
WSDL Messages
•WSDL messages are used to specify what the containers should be like that hold data when a WSDL operation is invoked. They are essentially lists of parts, each of which is an XSD simple or complex type.
•In the example above the 'PrintMessage' is defined as having a single part 'value', which is of type 'xsd:string'.
WSDL Port Types
•WSDL Port Types represent the definition of the web service itself. They describe the API or interface to the web service. A port type is a list of operations with 'input's and 'output's. Each of the 'input's and 'output's is a WSDL message that must have been previously defined (although it could have been imported from another WSDL file).
•A WSDL port type operation can also have any number of 'fault' elements. Each of these specifies an error message which would be an alternative to the 'output' message.
•Note that the name specified on the port type does not have any namespace prefix. This is because the port type is being defined here and now and it will inherit the target namespace. The 'printMessage' specified in the operation definition however DOES have a namespace prefix. This is because the printMessage has previously been defined and is being referenced. The 'tns:' prefix maps to the same namespace as the target namespace in the previously defined 'printMessage' message.
WSDL Port Type Bindings
•A 'binding' in WSDL specifies how the web service is actually implemented. Everything up until this point has been abstract and has dealt with only how to speak to the web service. The binding specifies what is on the other side that you are speaking to.
•A web service can be bound in many different ways. The most common bindings for a web service are: oas a SOAP/HTTP web service - whereby some implementation would be listening on a specified port and would accept SOAP messages over an HTTP transport. oas a Java web service - whereby some java class is mapped to the port type and is used directly as an implementation.
•In the binding above, a mapping has been created which specifies that the port type operation 'print' should be mapped to a Java method called 'print'. In addition to this, the XSD type 'string' has been mapped to the Java type 'String'.
•Using this mapping information a Java class can be specified later in the WSDL file as the 'address' of a concrete web service implementation. This class can be instantiated and when calls are made to the 'print' operation, they will be proxied to the 'print' method of this class. In the process of proxying the 'print' operation, any XSD strings will also be converted to Java strings as specified in the binding.
WSDL Service
•The WSDL 'service' element specifies a WSDL 'port'. A single port is an instance of a web service, which is implemented via a particular binding and which is available at a given address.
•In the case of our printout port, we are defining a web service which is bound using the previously defined Java binding and which can be found at the address 'org.eclipse...EnginePrinterPort‘.
•Note that the address is binding specific. The Java binding knows to interpret the 'className' attribute as a fully qualified Java class name and understands how to instantiate the class and proxy the WSDL operations to the Java methods specified in the 'binding' element.
Partner Link Types
•Partner Link Types are actually not a WSDL construct, but a BPEL construct. WSDL was around before BPEL and is purely designed towards describing web services. BPEL however requires that a partner link instance be associated with a particular WSDL port type. In this case there is only one end of the partner link which needs to be implemented - the 'printService' role. It is possible to have two roles in a single partner link type, each of which can be implemented by two communicating web services.
•The BPEL partnerLink definition specified a partner link type for the partner link and also either a 'myRole' or a 'partnerRole'. In our previous example the 'partnerRole' was defined as 'printService'. This is because the BPEL process will be speaking TO the 'printService', rather than acting as a 'printService' which other web clients can speak to (in that case the 'myRole' part of the partner link would have been defined).
Java Web Service Implementation
package org.eclipse.wsws.choreography.jengine.internal.extensions.wsdlbinding.wsif.ports; public class EnginePrinterPort { public void print(String s) { System.out.println(s); } }
The Java class specified in the WSDL 'service' element is the Java class that the BPEL engine will expect to find at runtime. We therefore need to create that java class and fill it with any methods that we specified mappings to in the WSDL 'binding' element (e.g. the 'print' method).
Deploying web service
•Once you have your BPEL file using the WSDL web service description you created and you have your compiled Java class that implements the web service you need to put it all together.
•The quickest and easiest way to do this is to use the 'Dependencies' tab in the Choreography launch configuration.
•Set up a launch configuration to run your Hello World BPEL file and then click on the 'Dependencies' tab. In here you can tell the engine which JARs are required for any user-provided java endpoints. Just click 'Add' and then choose the JAR containing your Hello World Java web service implementation. You should see the JAR show up in the table and you should ensure that the JAR is set to 'enabled'.
•Once you've added the dependency, just run the launch configuration. If you're running a distributed engine the engine will automatically pass the dependency JAR around for use on remote engines (engines on other host machines).
Redistributable Java Endpoint Deployment (Deploying as an Eclipse Plugin)
•If you want to write a Java web service implementation or build up a library of useful services that you want to be able to distribute or send to other people then you can expose dependencies via the Eclipse Extension Point mechanism.
•Just extend the extension point 'org.eclipse.wsws.choreography.internal_WSDLPortDependency' and add a reference to your JAR. The 'namespace' attributes specify which namespaces your JAR is required for. If any of the specified namespaces are used your JAR will be passed round the engine in anticipation of use by the BPEL program.
Enterprise Integration Patterns & MINI Cooper Clubman


Aggregator
In the morning, I have to wait for Mark, John and Aaron to arrive, and then we go to work together in my MINI. They arrive in different order, but all of them will come as planned.
Canonical Data Model
I use ODB II device to check MINI's health. Thousands parts send standard ODB II format data to the port.
Channel Purger
Remember how to clear trip computer information?
Claim Check
When we bought the new furniture set. I drove the MINI to U-Haul store and rented a truck.
Command Message
I can press a button to open MINI's barn doors remotely.
Competing Consumers
All of us (John, Mark, Aaron and me) are responsible for MINI's maintance calls. Whoever notices the maintance indicator on dashboard brings the car to dealer.
Composed Message Processor
MINI can be started by pressing "Start" button while holding clutch and break paddle. There are many internal signals to battery, engine, dash board and break system.
Content Enricher
Aaron looked up my MINI registration card. Now he know where I live in additon of I am an MINI owner.
Content Filter
John wants to go to work every day. But to consurve gas, I don't let him take a ride the MINI if he can work from home.
Content-Based Router
Usually we take highway I-75 to go to work. But if Mark didn't have his breakfast, we have to stop at a restaurant called Miss Chick. His girlfriend works there and he can get free breakfast.
Control Bus
MINI is happy to take highway to work. Building highway is expensive, but every car takes advantage afterwards.
Correlation Identifier
John, Aaron and I look a like. My wife checks my finger prints after my MINI arrives home and before dinner.
Datatype Channel
Sometimes just one of us drives MINI to work. Each of us drives different route.
Dead Letter Channel
All of us agree that if we cannot reach our work place for some reason, we will drive to airport parking lot A1.
Detour
Whenever we want to test our MINI for fun, we drive to Hell, MI on our way to work, even though it is in the opposite direction.
Document Message
John's job is to bring his laptop to work and then bring it back. His wife does all work at night and John's co-worker download files from John's laptop and work from there.
Durable Subscriber
Jack is Mark's friend. His house was taken back by bank. He doen't have a home now. We drive MINI to pick up his mail from Post Office and store them in the car. Whenever we know where Jack is, we deliver the mail to him.
Dynamic Router
Sometimes we change our route based on what we heard from WWJ News Radio 950.
Envelope Wrapper
When we drive to work place, four of us are wrapped in the MINI.
Event Messge
Aaron likes basketball game. Whenever he has tickets, he would let us know during our MINI ride. We can make decision whether we want to go, but the game would go on as scheduled anyway.
Even-Driven Consumer
Mark doesn't have free breadfast at his girlfriend's restaurant every day. His girlfriend doesn't call him everyday to check if he would come. Only when Mark stop by with MINI, then his girlfriend would prepare the breakfast for him.
File Transfer
Mark is helping his friend Jack find a job. He takes Jack's resume file on MINI and submits to HR department where he works.
Format Indicator
When I looked Jack's resume that Mark left in MINI, it includes resume version number, his social security number and is written in Microsoft Word format.
Guaranteed Delivery
To make sure that Jack's resume landed on right person's hand, Mark kept the resume in MINI for three days and handed over to HR Director who have just returned from a vacation.
Idempotent Receiver
Mark's girlfriend told him that he can only get one free breakfast each day. If the meal disappears between kitchen and dinning room, Mark won't get another one.
Invalid Message Channel
After purchased the MINI, we've received many junk mail to ask us to purchase MINI accessories. We throw them into a box next to our trash can.
Message Broker
We prefer that all MINI maintance work be informed by MINI dealer.
Message Bus
ODB II device displays information in English; Dealer Text Message displays information in English; MINI dashboard displays information in English.
Message Channel
We use GPS to define our driving route. Once the route is defined, it is saved in GPS and will be used repeatly.
Message Dispatcher
After work, I drive MINI back to Oakland Mall parking lot so that John, Mark and Aaron can get off and drive their cars to go home. Since MINI doesn't have rear doors, the front passenger must get out first, then the rear right passenger, and the rear left passenger.
Message Endpoint
I requires John, Mark and Aaron to give me their work address, so that I can drive them to their work place.
Message Expiration
John's company is downsizing. Any worker who has reached or passed 50 years old birthday will be laid off automatically. John is approaching his 50th birthday, we may lose our MINI ride companion:(
Message Filter
We know John's wife does all the work for John. One day, I asked John if his wife is from India. He was surprised and asked: "Without that, how can you do English And Indian (EAI)?". But that's the only detail he was willing to tell us about his wife.
Message History
MINI has an advanced GPS system. It can record all routes we go through every day.
Message Router
MINI's GPS system has real-time traffic. If we want, we can ask GPS to guide the route.
Message Sequence
Mark has 8 children. Occasionally I helped him transport his family with MINI. We needed total three round trips and I tagged every kid with a number to make sure that I didn't miss any one.
Message Store
To find out more information about John's India wife, we tapped his cell phone so that every text message he sents to his wife, a duplicated copy will be intercepted by a device installed on MINI. We told John that the device can prevent the loss of text messages and he agreed.
Message Translator
When we checked John's message on MINI, we found most messages are written in Hindi. We scrambled to install a Hindi to English translation software. Now we can understand the messages.
Message
You should know it if you know what text message is.
Message Bridge
During our MINI ride, I asked John how can he communicate with his co-worker. He replied: "I text message Hindi back and forth with my wife, and then speak with my colleague in English.
Message Gateway
Even though we take the same ride to work every day, we work in totally different area. I am an Software Architect, Aaron is a senior Java develper, Mark is a graphic designer, John, umm.., I don't know, I call him EAI integrator.
Messaging Mapper
My wife and I love to drive our MINI to IKEA in Canton MI. We find the big object we like, the store staff helps us dis-assemble it and puts it into a compact box, then we use our MINI to haul the stuff back home. It is my duty to re-assemble it back.
Messaging
Think about the languages we read and speak. Including MINI dashboard information.
Normalizer
MINI's GPS can recognize different languages. It replies back only in English though. The GPS itself stores just one set of data. It uses the language translator to translate incoming voice.
Pipes and Filters
Look it up under the MINI, you will under immediately.
Point-to-Point Channel
Without Hindi to English translator, sitting in MINI, only John can understand his wife's messae.
Polling Consumer
Every hour, John asks his Indian wife if she had made any progress.
Process Manager
At one time, Mark, Aaron and I worked on one project. To avoid direct confrontations, we asked John to be a moderator. He makes decision to assign tasks based on the benefit of the project.
Publish-Subscribe Channel
Aaron and I receive text message from WSJ on our smart phones because we both subscribed to wsj.com
Recipient List
Only Mark, Aaron and I can see the text messages between John and his wife.
Remote Procedure Invocation
When I was buy MINI, I called my dealere to find out details on cars.
Request-Reply
Phone conversation in MINI.
Resequencer
My MINI dealer told me a list of cars ordered by price, but I asked him to provide me a list ordered by make year.
Return Address
My MINI dealer knows my every call to him even though I didn't leave message. He had my caller ID stored.
Routing Slip
Every time we swipe our card at work, the ID and time stamp is recorded. In order to get paid, we must swipe-in in the morning, and swipe-out in the afternoon.
Scatter-Gather
When We were buying MINI, I asked several dealers to give me the quote, then I put their quotes together and presented to my wife the best deal.
Selective Consumer
When I was buying my MINI, my dealer had sent me all inventory, but I was only interested in lighting blue MINI Cooper Clubman.
Service Activator
When I drop my MINI at dealership for service, I don't need to tell them what to do. The service manager will check the information on dashboard and let technician do the work accordingly.
Shared Database
No matter which MINI dealer I went, they all had my MINI's service history.
Smart Proxy
If Mark, John, Aaron wants to borrow my MINI, I always ask them to pick-up and drop-off the car in Oakland parking lot. None of them knows where I live.
Splitter
When Mark got his free breakfast from Miss Chick restaurant during our MINI ride, we divided it into 4 and each of us had a portion.
Test Message
Every morning at 3AM, I starts my MINI, check dashboard information to make sure that I can run it without problem in the morning.
Transactional Client
Conversation between any two of us in the MINI.
Wire Tap
When another person is driving, I check the GPS display to make sure the direction is right.
In the morning, I have to wait for Mark, John and Aaron to arrive, and then we go to work together in my MINI. They arrive in different order, but all of them will come as planned.
Canonical Data Model
I use ODB II device to check MINI's health. Thousands parts send standard ODB II format data to the port.
Channel Purger
Remember how to clear trip computer information?
Claim Check
When we bought the new furniture set. I drove the MINI to U-Haul store and rented a truck.
Command Message
I can press a button to open MINI's barn doors remotely.
Competing Consumers
All of us (John, Mark, Aaron and me) are responsible for MINI's maintance calls. Whoever notices the maintance indicator on dashboard brings the car to dealer.
Composed Message Processor
MINI can be started by pressing "Start" button while holding clutch and break paddle. There are many internal signals to battery, engine, dash board and break system.
Content Enricher
Aaron looked up my MINI registration card. Now he know where I live in additon of I am an MINI owner.
Content Filter
John wants to go to work every day. But to consurve gas, I don't let him take a ride the MINI if he can work from home.
Content-Based Router
Usually we take highway I-75 to go to work. But if Mark didn't have his breakfast, we have to stop at a restaurant called Miss Chick. His girlfriend works there and he can get free breakfast.
Control Bus
MINI is happy to take highway to work. Building highway is expensive, but every car takes advantage afterwards.
Correlation Identifier
John, Aaron and I look a like. My wife checks my finger prints after my MINI arrives home and before dinner.
Datatype Channel
Sometimes just one of us drives MINI to work. Each of us drives different route.
Dead Letter Channel
All of us agree that if we cannot reach our work place for some reason, we will drive to airport parking lot A1.
Detour
Whenever we want to test our MINI for fun, we drive to Hell, MI on our way to work, even though it is in the opposite direction.
Document Message
John's job is to bring his laptop to work and then bring it back. His wife does all work at night and John's co-worker download files from John's laptop and work from there.
Durable Subscriber
Jack is Mark's friend. His house was taken back by bank. He doen't have a home now. We drive MINI to pick up his mail from Post Office and store them in the car. Whenever we know where Jack is, we deliver the mail to him.
Dynamic Router
Sometimes we change our route based on what we heard from WWJ News Radio 950.
Envelope Wrapper
When we drive to work place, four of us are wrapped in the MINI.
Event Messge
Aaron likes basketball game. Whenever he has tickets, he would let us know during our MINI ride. We can make decision whether we want to go, but the game would go on as scheduled anyway.
Even-Driven Consumer
Mark doesn't have free breadfast at his girlfriend's restaurant every day. His girlfriend doesn't call him everyday to check if he would come. Only when Mark stop by with MINI, then his girlfriend would prepare the breakfast for him.
File Transfer
Mark is helping his friend Jack find a job. He takes Jack's resume file on MINI and submits to HR department where he works.
Format Indicator
When I looked Jack's resume that Mark left in MINI, it includes resume version number, his social security number and is written in Microsoft Word format.
Guaranteed Delivery
To make sure that Jack's resume landed on right person's hand, Mark kept the resume in MINI for three days and handed over to HR Director who have just returned from a vacation.
Idempotent Receiver
Mark's girlfriend told him that he can only get one free breakfast each day. If the meal disappears between kitchen and dinning room, Mark won't get another one.
Invalid Message Channel
After purchased the MINI, we've received many junk mail to ask us to purchase MINI accessories. We throw them into a box next to our trash can.
Message Broker
We prefer that all MINI maintance work be informed by MINI dealer.
Message Bus
ODB II device displays information in English; Dealer Text Message displays information in English; MINI dashboard displays information in English.
Message Channel
We use GPS to define our driving route. Once the route is defined, it is saved in GPS and will be used repeatly.
Message Dispatcher
After work, I drive MINI back to Oakland Mall parking lot so that John, Mark and Aaron can get off and drive their cars to go home. Since MINI doesn't have rear doors, the front passenger must get out first, then the rear right passenger, and the rear left passenger.
Message Endpoint
I requires John, Mark and Aaron to give me their work address, so that I can drive them to their work place.
Message Expiration
John's company is downsizing. Any worker who has reached or passed 50 years old birthday will be laid off automatically. John is approaching his 50th birthday, we may lose our MINI ride companion:(
Message Filter
We know John's wife does all the work for John. One day, I asked John if his wife is from India. He was surprised and asked: "Without that, how can you do English And Indian (EAI)?". But that's the only detail he was willing to tell us about his wife.
Message History
MINI has an advanced GPS system. It can record all routes we go through every day.
Message Router
MINI's GPS system has real-time traffic. If we want, we can ask GPS to guide the route.
Message Sequence
Mark has 8 children. Occasionally I helped him transport his family with MINI. We needed total three round trips and I tagged every kid with a number to make sure that I didn't miss any one.
Message Store
To find out more information about John's India wife, we tapped his cell phone so that every text message he sents to his wife, a duplicated copy will be intercepted by a device installed on MINI. We told John that the device can prevent the loss of text messages and he agreed.
Message Translator
When we checked John's message on MINI, we found most messages are written in Hindi. We scrambled to install a Hindi to English translation software. Now we can understand the messages.
Message
You should know it if you know what text message is.
Message Bridge
During our MINI ride, I asked John how can he communicate with his co-worker. He replied: "I text message Hindi back and forth with my wife, and then speak with my colleague in English.
Message Gateway
Even though we take the same ride to work every day, we work in totally different area. I am an Software Architect, Aaron is a senior Java develper, Mark is a graphic designer, John, umm.., I don't know, I call him EAI integrator.
Messaging Mapper
My wife and I love to drive our MINI to IKEA in Canton MI. We find the big object we like, the store staff helps us dis-assemble it and puts it into a compact box, then we use our MINI to haul the stuff back home. It is my duty to re-assemble it back.
Messaging
Think about the languages we read and speak. Including MINI dashboard information.
Normalizer
MINI's GPS can recognize different languages. It replies back only in English though. The GPS itself stores just one set of data. It uses the language translator to translate incoming voice.
Pipes and Filters
Look it up under the MINI, you will under immediately.
Point-to-Point Channel
Without Hindi to English translator, sitting in MINI, only John can understand his wife's messae.
Polling Consumer
Every hour, John asks his Indian wife if she had made any progress.
Process Manager
At one time, Mark, Aaron and I worked on one project. To avoid direct confrontations, we asked John to be a moderator. He makes decision to assign tasks based on the benefit of the project.
Publish-Subscribe Channel
Aaron and I receive text message from WSJ on our smart phones because we both subscribed to wsj.com
Recipient List
Only Mark, Aaron and I can see the text messages between John and his wife.
Remote Procedure Invocation
When I was buy MINI, I called my dealere to find out details on cars.
Request-Reply
Phone conversation in MINI.
Resequencer
My MINI dealer told me a list of cars ordered by price, but I asked him to provide me a list ordered by make year.
Return Address
My MINI dealer knows my every call to him even though I didn't leave message. He had my caller ID stored.
Routing Slip
Every time we swipe our card at work, the ID and time stamp is recorded. In order to get paid, we must swipe-in in the morning, and swipe-out in the afternoon.
Scatter-Gather
When We were buying MINI, I asked several dealers to give me the quote, then I put their quotes together and presented to my wife the best deal.
Selective Consumer
When I was buying my MINI, my dealer had sent me all inventory, but I was only interested in lighting blue MINI Cooper Clubman.
Service Activator
When I drop my MINI at dealership for service, I don't need to tell them what to do. The service manager will check the information on dashboard and let technician do the work accordingly.
Shared Database
No matter which MINI dealer I went, they all had my MINI's service history.
Smart Proxy
If Mark, John, Aaron wants to borrow my MINI, I always ask them to pick-up and drop-off the car in Oakland parking lot. None of them knows where I live.
Splitter
When Mark got his free breakfast from Miss Chick restaurant during our MINI ride, we divided it into 4 and each of us had a portion.
Test Message
Every morning at 3AM, I starts my MINI, check dashboard information to make sure that I can run it without problem in the morning.
Transactional Client
Conversation between any two of us in the MINI.
Wire Tap
When another person is driving, I check the GPS display to make sure the direction is right.
Tuesday, March 24, 2009
Integrate Single-Sign-On Web Service with Business Objects InfoView (JAVA)
Step 1: Query SSO Web Service
queryWebService
public boolean queryWebService(java.lang.String sUserID,
java.lang.String sPassword,
java.lang.String sPortalPassword)Use application request info and user credential to authenticate the user
With Webservice is already initialized, query the webservice, using application request info and user credential to get user response object back. Return true if succeeded.
Returns:
boolean Status of user authentication.
Step 2 Get SSO Session ID
getAWSSessionID
public static java.lang.String getAWSSessionID(HttpServletRequest oRequest)Get AWS session ID. The AWS session ID is stored by SSO login page.
This method retrieves AWS session ID cookie by using specific cookie name. It also uses UTF-8 to decode the session id.
Returns:
String UTF-8 decoded session id
Since:
0.1
Step 3 Get User ID by session
getUserIDBySession
public java.lang.String getUserIDBySession(java.lang.String sAWSSessionID)
throws java.io.IOExceptionReturn user id if existing AWS session of application request info is authenticated.
If AWS session is found, the session id will be used to check against application request info. If the session is still alive on AWS server the user id will be returned for further application authentication.
Returns:
String User id in the session with application request info.
Step 4 Forward to Internal BusinessObjects Logon Page
request.getRequestDispatcher("/" + oPropertyLoader.getPropertyValue("BOLogonPage").trim()).forward(request, response);
Step 5 Initialize Business Object Session Manager
init
public boolean init()Initialize BOUserInfo. Not related to specific user.
This method initializes Property Loader and gets session manager
Returns:
boolean Indicates the status of initialization
Since:
0.1
Step 6 Get Business Object Server Logon Token
getLogonToken
public java.lang.String getLogonToken()Get user logon taken.
This method uses userid, password, cms and authenticatio type to get logon token. If the userid and password is in specified cms database, it returns the token, otherwise it returns blank string. It also save the infoStore object for future usage.
Returns:
String Logon Taken
Since:
0.1
Step 7 Logon to Business Object InfoView
sHomeURL = oPropertyLoader.getPropertyValue("ServerURL") + oPropertyLoader.getPropertyValue("BoInfoviewString") + logonToken;
/*
* It is useful to store some frequently used objects in the session for
* easy access later on.
*/
// Store the IEnterpriseSession object in the session.
session.setAttribute("EnterpriseSession", oBOUserInfo.getEnterpriseSession());
// Create an IInfoStore object and store it in the session.
IInfoStore iStore = (IInfoStore)oBOUserInfo.getEnterpriseSession().getService("InfoStore");
session.setAttribute("InfoStore", iStore);
response.sendRedirect(sHomeURL
queryWebService
public boolean queryWebService(java.lang.String sUserID,
java.lang.String sPassword,
java.lang.String sPortalPassword)Use application request info and user credential to authenticate the user
With Webservice is already initialized, query the webservice, using application request info and user credential to get user response object back. Return true if succeeded.
Returns:
boolean Status of user authentication.
Step 2 Get SSO Session ID
getAWSSessionID
public static java.lang.String getAWSSessionID(HttpServletRequest oRequest)Get AWS session ID. The AWS session ID is stored by SSO login page.
This method retrieves AWS session ID cookie by using specific cookie name. It also uses UTF-8 to decode the session id.
Returns:
String UTF-8 decoded session id
Since:
0.1
Step 3 Get User ID by session
getUserIDBySession
public java.lang.String getUserIDBySession(java.lang.String sAWSSessionID)
throws java.io.IOExceptionReturn user id if existing AWS session of application request info is authenticated.
If AWS session is found, the session id will be used to check against application request info. If the session is still alive on AWS server the user id will be returned for further application authentication.
Returns:
String User id in the session with application request info.
Step 4 Forward to Internal BusinessObjects Logon Page
request.getRequestDispatcher("/" + oPropertyLoader.getPropertyValue("BOLogonPage").trim()).forward(request, response);
Step 5 Initialize Business Object Session Manager
init
public boolean init()Initialize BOUserInfo. Not related to specific user.
This method initializes Property Loader and gets session manager
Returns:
boolean Indicates the status of initialization
Since:
0.1
Step 6 Get Business Object Server Logon Token
getLogonToken
public java.lang.String getLogonToken()Get user logon taken.
This method uses userid, password, cms and authenticatio type to get logon token. If the userid and password is in specified cms database, it returns the token, otherwise it returns blank string. It also save the infoStore object for future usage.
Returns:
String Logon Taken
Since:
0.1
Step 7 Logon to Business Object InfoView
sHomeURL = oPropertyLoader.getPropertyValue("ServerURL") + oPropertyLoader.getPropertyValue("BoInfoviewString") + logonToken;
/*
* It is useful to store some frequently used objects in the session for
* easy access later on.
*/
// Store the IEnterpriseSession object in the session.
session.setAttribute("EnterpriseSession", oBOUserInfo.getEnterpriseSession());
// Create an IInfoStore object and store it in the session.
IInfoStore iStore = (IInfoStore)oBOUserInfo.getEnterpriseSession().getService("InfoStore");
session.setAttribute("InfoStore", iStore);
response.sendRedirect(sHomeURL
Labels:
.ALL.,
ALL,
Business Intelligence,
Business Objects,
Web Services
UNIX Scheduling
Process states:

The scheduler picks the next process to move from ready to running
• What’s the “Application Profile”:
– A program alternates between CPU usage and I/O
– Relevant question for scheduling: is a program compute-bound
(mostly CPU usage) or I/O-bound (mostly I/O wait)
• When scheduling occurs:
– When a process is created
– When a process terminates
– When a process issues a blocking call (I/O, semaphores)
– On a clock interrupt
– On I/O interrupt (e.g., disk transfer finished, mouse click)
– System calls for IPC (e.g., up on semaphore, signal, etc.)
• Multi-level scheduling (e.g., 2-level in Unix)
– Swapper decides which processes should reside in memory
– Scheduler decides which ready process gets the CPU next
Scheduling Issues
• Can preemption occur?
– Preemptive schedulers can take control from a process at interrupt
– Non-preemptive scheduler doesn’t
• What are we trying to optimize?
– CPU utilization: Fraction of time CPU is in use
– Throughput: average number of jobs completed per time unit
– Turnaround Time: average time between job submission and
completion
– Waiting Time: average amount of time a process is ready but waiting
– Response Time: time until the system responds to a command
– Response Ratio: (Turnaround Time)/(Execution Time) -- long jobs
should wait
Basic Scheduling Algorithm
• FCFS - First-Come, First-Served
– Non-preemptive
– Ready queue is a FIFO queue
– Jobs arriving are placed at the end of queue
– Dispatcher selects first job in queue and this job
runs to completion of CPU burst
• Advantages: simple, low overhead
• Disadvantages: inappropriate for interactive
systems, large fluctuations in average turnaround time are possible.
• Example workload
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• FCFS schedule:
Job 1 Job 2 Job 3
0 24 27 30
• Total waiting time: 0 + 24 + 27 = 51
• Average waiting time: 51/3 = 17
• Total turnaround time: 24 + 27 + 30 = 81
• Average turnaround time: 81/3 = 27
• SJF - Shortest Job First
• Non-preemptive
• Ready queue treated as a priority queue based on
smallest CPU-time requirement
• arriving jobs inserted at proper position in queue
• dispatcher selects shortest job (1st in queue) and runs to
completion
• Advantages
• provably optimal average turnaround time
• Disadvantages:
• starvation possible
• can’t actually be implemented.
• Can do it approximately: use exponential averaging to
predict length of next CPU burst
• pick shortest predicted burst next
• Example workload
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• SJF schedule:
Job 2 Job 3 Job 1
0 3 6 30
• Total waiting time: 6 + 0 + 3 = 9
• Average waiting time: 3
• Total turnaround time: 30 + 3 + 6 = 39
• Average turnaround time: 39/3 = 13
• SJF always gives minimum waiting time and turnaround time Exponent
Exponential Averaging
t n+1 = a tn + (1 - a) ) t n
• t n+1 : predicted length of next CPU burst
• tn : actual length of last CPU burst
• t n : previous prediction
• a = 0 implies make no use of recent history
(t n+1 = t n)
• a = 1 implies t n+1 = tn (past prediction not used).
• a = 1/2 implies weighted (older bursts get less and
less weight).
• RR - Round Robin
• Preemptive version of FCFS
• Circular ready queue
– arriving jobs are placed at end
– dispatcher selects first job in queue and runs until completion of CPU burst, or until time quantum expires
– if quantum expires, job is again placed at end
• Example workload:
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• RR schedule with time quantum=3:
Job 1 Job 2 Job 3 Job 1
0 3 6 9 30
• Total waiting time: 6 + 3 + 6 = 15
• Average waiting time: 5
• Total turnaround time: 30 + 6 + 9 = 45
• Average turnaround time: 15
• RR gives intermediate wait and turnaround time (compared to SJF and FCFS)
• Advantages: simple, low overhead, works for
interactive systems
• Disadvantages: if quantum is too small, too much
time wasted in context switching; if too large (i.e.
longer than mean CPU burst), approaches FCFS.
• Typical value: 20 – 40 msec
• Rule of thumb: Choose quantum so that large
majority (80 – 90%) of jobs finish CPU burst in
one quantum
• RR makes the assumption that all processes are
equally important
Importance of a good Quantum Factor
• Context switching is expensive
– hundreds of instructions
– if quantum is too small, much of the CPU time will
be wasted on context switching overhead
• … and the machine will seem slower than it really is
• Interactivity requires rapid response time
– Interactive processes need service quickly,
especially after I/O occurs
– if quantum is too large, waiting time is increased
• … and the machine will seem slower than it really is
• Quantum must be >> context switch cost, but
<<>
• HPF - Highest Priority First
• General class of algorithms ==> priority scheduling
• Each job assigned a priority which may change dynamically
• May be preemptive or non-preemptive
• Central problem: how to select / compute priorities?
• Multi-Level Feedback (FB)
• Each priority level has a ready queue, and a time quantum
• process enters highest priority queue initially, and (next) lower queue
with each timer interrupt (penalized for long CPU usage)
• bottom queue is standard Round Robin
• process in a given queue not scheduled until all higher queues are empty
Scheduling in Unix
• Based on multi-level feedback queues
• Priorities range from -64 to 63 (lower number means higher
priority)
• Negative numbers reserved for processes waiting in kernel mode
(that is, just woken up by interrupt handlers) (why do they have a
higher priority?)
• Time quantum = 1/10 sec (empirically found to be the longest
quantum that could be used without loss of the desired response
for interactive jobs such as editors)
– short time quantum means better interactive response
– long time quantum means higher overall system throughput since
less context switch overhead and less processor cache flush.
• Priority dynamically adjusted to reflect
– resource requirement (e.g., blocked awaiting an event)
– resource consumption (e.g., CPU time)
Unix CPU Scheduler
• Two values (stored in the PCB/process table entry)
– p_cpu: an estimate of the recent CPU use
– p_nice: a user/OS settable weighting factor (-20..20) for flexibility;
default = 0; negative increases priority; positive decreases priority
• Each process' priority calculated periodically
priority = base + p_cpu + p_nice
and the process is moved into the appropriate ready queue
• CPU utilization, p_cpu, is incremented each time the system clock
ticks and the process is found to be executing.
• p_cpu is adjusted once every second (time decay)
– Possible adjustment: divide by 2 (that is, shift right)
– Motivation: Recent usage penalizes more than past usage
– Precise details differ in different versions (e.g. 4.3 BSD uses current
load (number of ready processes) also in the adjustment formula)

The scheduler picks the next process to move from ready to running
• What’s the “Application Profile”:
– A program alternates between CPU usage and I/O
– Relevant question for scheduling: is a program compute-bound
(mostly CPU usage) or I/O-bound (mostly I/O wait)
• When scheduling occurs:
– When a process is created
– When a process terminates
– When a process issues a blocking call (I/O, semaphores)
– On a clock interrupt
– On I/O interrupt (e.g., disk transfer finished, mouse click)
– System calls for IPC (e.g., up on semaphore, signal, etc.)
• Multi-level scheduling (e.g., 2-level in Unix)
– Swapper decides which processes should reside in memory
– Scheduler decides which ready process gets the CPU next
Scheduling Issues
• Can preemption occur?
– Preemptive schedulers can take control from a process at interrupt
– Non-preemptive scheduler doesn’t
• What are we trying to optimize?
– CPU utilization: Fraction of time CPU is in use
– Throughput: average number of jobs completed per time unit
– Turnaround Time: average time between job submission and
completion
– Waiting Time: average amount of time a process is ready but waiting
– Response Time: time until the system responds to a command
– Response Ratio: (Turnaround Time)/(Execution Time) -- long jobs
should wait
Basic Scheduling Algorithm
• FCFS - First-Come, First-Served
– Non-preemptive
– Ready queue is a FIFO queue
– Jobs arriving are placed at the end of queue
– Dispatcher selects first job in queue and this job
runs to completion of CPU burst
• Advantages: simple, low overhead
• Disadvantages: inappropriate for interactive
systems, large fluctuations in average turnaround time are possible.
• Example workload
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• FCFS schedule:
Job 1 Job 2 Job 3
0 24 27 30
• Total waiting time: 0 + 24 + 27 = 51
• Average waiting time: 51/3 = 17
• Total turnaround time: 24 + 27 + 30 = 81
• Average turnaround time: 81/3 = 27
• SJF - Shortest Job First
• Non-preemptive
• Ready queue treated as a priority queue based on
smallest CPU-time requirement
• arriving jobs inserted at proper position in queue
• dispatcher selects shortest job (1st in queue) and runs to
completion
• Advantages
• provably optimal average turnaround time
• Disadvantages:
• starvation possible
• can’t actually be implemented.
• Can do it approximately: use exponential averaging to
predict length of next CPU burst
• pick shortest predicted burst next
• Example workload
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• SJF schedule:
Job 2 Job 3 Job 1
0 3 6 30
• Total waiting time: 6 + 0 + 3 = 9
• Average waiting time: 3
• Total turnaround time: 30 + 3 + 6 = 39
• Average turnaround time: 39/3 = 13
• SJF always gives minimum waiting time and turnaround time Exponent
Exponential Averaging
t n+1 = a tn + (1 - a) ) t n
• t n+1 : predicted length of next CPU burst
• tn : actual length of last CPU burst
• t n : previous prediction
• a = 0 implies make no use of recent history
(t n+1 = t n)
• a = 1 implies t n+1 = tn (past prediction not used).
• a = 1/2 implies weighted (older bursts get less and
less weight).
• RR - Round Robin
• Preemptive version of FCFS
• Circular ready queue
– arriving jobs are placed at end
– dispatcher selects first job in queue and runs until completion of CPU burst, or until time quantum expires
– if quantum expires, job is again placed at end
• Example workload:
Job 1: 24 units, Job 2: 3 units, Job 3: 3 units
• RR schedule with time quantum=3:
Job 1 Job 2 Job 3 Job 1
0 3 6 9 30
• Total waiting time: 6 + 3 + 6 = 15
• Average waiting time: 5
• Total turnaround time: 30 + 6 + 9 = 45
• Average turnaround time: 15
• RR gives intermediate wait and turnaround time (compared to SJF and FCFS)
• Advantages: simple, low overhead, works for
interactive systems
• Disadvantages: if quantum is too small, too much
time wasted in context switching; if too large (i.e.
longer than mean CPU burst), approaches FCFS.
• Typical value: 20 – 40 msec
• Rule of thumb: Choose quantum so that large
majority (80 – 90%) of jobs finish CPU burst in
one quantum
• RR makes the assumption that all processes are
equally important
Importance of a good Quantum Factor
• Context switching is expensive
– hundreds of instructions
– if quantum is too small, much of the CPU time will
be wasted on context switching overhead
• … and the machine will seem slower than it really is
• Interactivity requires rapid response time
– Interactive processes need service quickly,
especially after I/O occurs
– if quantum is too large, waiting time is increased
• … and the machine will seem slower than it really is
• Quantum must be >> context switch cost, but
<<>
• HPF - Highest Priority First
• General class of algorithms ==> priority scheduling
• Each job assigned a priority which may change dynamically
• May be preemptive or non-preemptive
• Central problem: how to select / compute priorities?
• Multi-Level Feedback (FB)
• Each priority level has a ready queue, and a time quantum
• process enters highest priority queue initially, and (next) lower queue
with each timer interrupt (penalized for long CPU usage)
• bottom queue is standard Round Robin
• process in a given queue not scheduled until all higher queues are empty
Scheduling in Unix
• Based on multi-level feedback queues
• Priorities range from -64 to 63 (lower number means higher
priority)
• Negative numbers reserved for processes waiting in kernel mode
(that is, just woken up by interrupt handlers) (why do they have a
higher priority?)
• Time quantum = 1/10 sec (empirically found to be the longest
quantum that could be used without loss of the desired response
for interactive jobs such as editors)
– short time quantum means better interactive response
– long time quantum means higher overall system throughput since
less context switch overhead and less processor cache flush.
• Priority dynamically adjusted to reflect
– resource requirement (e.g., blocked awaiting an event)
– resource consumption (e.g., CPU time)
Unix CPU Scheduler
• Two values (stored in the PCB/process table entry)
– p_cpu: an estimate of the recent CPU use
– p_nice: a user/OS settable weighting factor (-20..20) for flexibility;
default = 0; negative increases priority; positive decreases priority
• Each process' priority calculated periodically
priority = base + p_cpu + p_nice
and the process is moved into the appropriate ready queue
• CPU utilization, p_cpu, is incremented each time the system clock
ticks and the process is found to be executing.
• p_cpu is adjusted once every second (time decay)
– Possible adjustment: divide by 2 (that is, shift right)
– Motivation: Recent usage penalizes more than past usage
– Precise details differ in different versions (e.g. 4.3 BSD uses current
load (number of ready processes) also in the adjustment formula)
Business Objects XI R2 Install on Solaris 10 (WebLogic) Pre-Installation Considerations
BusinessObjects Enterprise requires a database server software and web application server software to be installed and configured.
Oracle 10g database and Weblogic application server are required to be installed before BusinessObjects Enterprise installation. The database (MySQL) and application server (TomCat) which come with the installation package should not be chosen during BusinessObjects Enterprise installation. After completed the installation, the Weblogic application server needs to be configured so it integrates with BusinessObjects Enterprise.
In addition, ensure that all BusinessObjects Enterprise machines can communicate properly with one another:
• Each BusinessObjects Enterprise machine must be able to communicate over TCP/IP with the machine that runs your Central Management Server(CMS). The CMS database must exist prior to BusinessObjects Enterprise installation. The CMS is responsible for maintaining a database of information about your BusinessObjects Enterprise system, which other components can access as required. The data stored by the CMS includes information about users and groups, security levels, BusinessObjects Enterprise content, and servers. For more information about the CMS, see BusinessObjects Enterprise Administrator’s Guide.
• UNIX servers that run BusinessObjects Enterprise must have a fixed host name. Root privileges are required to set or modify a fixed host name on the system.
• Installing BusinessObjects Enterprise should not use root privilege. Ask UNIX administrator to create a user account for BusinessObjects Enterprise and perform a user install of BusinessObjects Enterprise.
• Ensure that your database client and server are set up to use Unicode character encoding (such as UTF-8). Consult your database documentation to determine the settings required for a Unicode configuration.
• When installing Oracle database server, server needs to be configured to use Unicode encoding for the character data types.
• The BusinessObjects Enterprise will be connected to a Weblogic application server. The Weblogic application server must be able to communicate with all BusinessObjects Enterprise machines. This communication is enabled by the BusinessObjects Enterprise SDK, which must be installed and configured on the Weblogic application server. In this case, the BusinessObjects Enterprise Java SDK must be installed.
Note:
• Make sure that Weblogic application server has the JDK on it, you will need to install it before installing BusinessObjects Enterprise SDK.
Checking for required commands and utilities
In order for the install setup program to run correctly, the following commands and utilities must be installed on your Solaris 10 system:
/bin/sh
Pwd
read
touch
uname
expr
hostname
sed
Awk
chown
grep
tail
tar
Id
dirname
Gzip
sty
ulimit
which
These relatively standard commands and utilities should be available on most UNIX distributions. However, if for any reason one of them is not available on your system, download and install a version appropriate to your system.
Additionally, these commands and utilities must be accessible in the PATH environment variable of the user account that you use when installing BusinessObjects Enterprise.
Important
Proper verification of both install privileges as well as connect strings need to performed.For Oracle Connectivity make sure that SQL*PLUS can be used to connect to the database.
Components installation before BusinessObjects XI R2 Install
Several components need to be installed before BusinessObjects Enterprise system can be installed. Here is the list that needs to be followed:
1. Installing Oracle Net Client 9.2
Note: Oracle Net Client 9.2 works as tested. Even though the BO XI R2 supported platforms document lists Oracle Net Client 10.2 as supported, there are issues using 10.2 client (64bit). It is recommended to use Oracle Net Client 9.2 with /lib32 set within the .profile
Follow the instruction below to install oracle 9i (9.2.0.6) client on application server.
· Login to application server usplgmhsras001/usplgmhsras002 with “Vbobje” id
· cd /usr/local/oracle/product.
create this directory if not exist.
· untar "9.2.0.6_client.tar” file
cd /usr/local/oracle/product
tar –xvf 9.2.0.6_client.tar
Validation:
With the Vbobje id, run sqlplus, should see the output like below:
SQL*Plus: Release 9.2.0.6.0 - Production on Wed May 23 16:03:53 2007
Copyright (c) 1982, 2002, Oracle Corporation. All rights reserved.
Enter user-name:
Vbobje unix id profile update:
Update Vbobje .profile file with the following entries: (if it’s not updated earlier)
ORACLE_HOME=/usr/local/oracle/product/9.2.0
export ORACLE_HOME
TNS_ADMIN=/var/opt/oracle
export TNS_ADMIN
LD_LIBRARY_PATH=$ORACLE_HOME/lib32
export LD_LIBRARY_PATH
ORACLE_SID=ORCL
export ORACLE_SID
PATH=$ORACLE_HOME/bin:/usr/j2se/bin:$PATH
export PATH
LANG=en_US.UTF-8
LC_ALL=en_US.UTF-8
export LANG LC_ALL
export BOBJE_ENV_SOURCED=""
. $HOME/bobje/bobje/setup/env.sh
tnsnames.ora file update:
· cd /var/opt/oracle
create this directory if not exist.
· Copy the tnsnames.ora file from /usr/local/oracle/product/9.2.0/ to /var/opt/oracle/ and modify the entries mention below:
PreProd / Production:
Database sid name
Database SID VIP
ORCL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS =
(PROTOCOL = tcp)
(HOST = ORCL)
(PORT = 1521)
)
)
(CONNECT_DATA =
(SID = ORCL)
)
)
Validation:
With the Vbobje id, run
· sqlplus bobje/bobje@ORCL
Should be able to SQL > prompt
· on sql prompt run the following select query
SQL> select name from v$database;
Output should look like this:
NAME
---------
ORCL
1. Setting up an empty database for CMS
2. Setting up an empty database for auditing
3. Creating an account, a home directory and a login environment for BOE installation
4. Providing and verifying connectivity to the CMS database
5. Installing the Java SDK
6. Accessing Weblogic Administration Console. It requires account and password
Setting up an empty database for CMS
BusinessObjects Enterprise requires a database (or Oracle schema) to store information about the system and its users. An existing Oracle 10g database will be used.
Database administrator must create a new database on database server before BusinessObjects Enterprise installation. The database used only for BusinessObjects Enterprise , and not contain other tables.Create a new database, create a new user account and password for the database that will be used by BusinessObjects Enterprise. Ensure that the new account has permission to create, modify, and delete tables and create procedures so that BusinessObjects Enterprise can modify the database as required. Write down name of the database, the user account, and the password. They will be used in BusinessObjects Enterprise installation script.
Name the new database (hisrepcmpldb.iweb.gm.com, instance: hisrepcm), and create a new user account (bobje), however, this naming convention is not required.
Ensure that the database server is set up to use Unicode character encoding (such as UTF-8). Consult your database documentation to determine the settings required for a Unicode configuration. For Oracle database servers, during installation you need to configure the server to use Unicode encoding for the character data types.
Setting up an empty database for auditing (if applies)
Create another database schema for auditing. It can share CMS instance. Name the auditing database (ex: bobjeaudit), and create a new user account (ex: bobjeaudit).
Creating an account, a home directory and a login environment
Create a specific user account and group under which the BusinessObjects Enterprise daemons can run. You will log on as this user in order to perform the remainder of the installation procedures. Although it requires root privileges to set up this account, the account itself does not require root privileges. Neither the installation scripts nor BusinessObjects Enterprise itself needs to run as root.Use usual administrative procedures to perform these recommended tasks.
Setting up UNIX system
Create a new group. Create a new user account, and set this user’s primary group to the new group. Assign a secure password to the new user account.
Create the directory where BusinessObjects Enterprise will be installed. By default, the installation will use current directory, that is, the directory you call the install program from, as its base directory for the install. You can override this default, with the directory of your choice at install time. You will see this directory referred to as INSTALLDIR throughout this document.
Set the new user’s HOME directory to the installation directory that you created. When you run the installation script, you choose a “user” installation type so that all of the installed files are confined to the directory that you specify here.
Ensure that the account you created has read, write, and execute permissions on the new HOME directory.
Assign the new user a default login shell, and create or modify the appropriate login script(s) for the user account. In particular, make sure that the login script(s) set up a default login environment that meets these requirements:
The user’s HOME directory must be included in the PATH environment variable.
All of the commands and utilities required by the install setup program must be accessible in the PATH environment variable. For details, see section 10.1.
The user’s login environment must set up the database environment such that the install setup program can access your database client software. Make sure the tnsnames.ora is set correctly. For details, see section 10.2.
Providing and verifying connectivity to the CMS database
To create tables and write data to the new CMS and auditing databases, the installation scripts need to establish a connection to the database server. That is, when you log on to UNIX with the user name from which you will perform the installation, the default shell environment must include the appropriate database environment variables and/or initialization files. Only then can the installation setup program access the CMS database using your database
client software.
The environment variables and/or files required by the installation scripts depend upon the type of database server you are running:
Oracle database is connected through a native connection, the installation searches the current shell for the ORACLE_HOME environment variable. This standard Oracle environment variable must be set in order for the install script to utilize the Oracle client software.
Additional database environment variables must be set in order for the installation script to use the database client software properly. Before running the installation script, test the shell environment of the account from which you will install BusinessObjects Enterprise to verify database connectivity and privileges. See the procedure that corresponds to the database.
The existing database needs to be sourced:
User can modify their own profile and add the command to source their database environment. This method must be done by the user which installs BusinessObjects Enterprise
Note: Consult database documentation and/or database administrator if the account shell environment from which you will install BusinessObjects Enterprise has not yet been set up for database client software, or if you are unable to connect successfully to the database.
Configuring the Java environment variable
After installing the Java SDK you must set the JAVA_HOME environment variable. If your Java web application server installs the Java SDK as part of its installation process, install the application server first, and then set the environment variable.
You need to know the directory path containing your Java SDK bin directory.
To set the JAVA_HOME environment variable on UNIX
1. Log on to the UNIX server with the user account and password which you will use to do your install.
2. Type JAVA_HOME=. is the directory containing your Java SDK bin directory.
3. To confirm that you’ve set the environment variable correctly, type echo $JAVA_HOME.
4. Using a text editor such as vi, add the command to set JAVA_HOME to the login environment for the account from which you will install BusinessObjects Enterprise. Add the command to your .profile file. This ensures that the value of JAVA_HOME is correctly set each time you log on to the account.
Oracle 10g database and Weblogic application server are required to be installed before BusinessObjects Enterprise installation. The database (MySQL) and application server (TomCat) which come with the installation package should not be chosen during BusinessObjects Enterprise installation. After completed the installation, the Weblogic application server needs to be configured so it integrates with BusinessObjects Enterprise.
In addition, ensure that all BusinessObjects Enterprise machines can communicate properly with one another:
• Each BusinessObjects Enterprise machine must be able to communicate over TCP/IP with the machine that runs your Central Management Server(CMS). The CMS database must exist prior to BusinessObjects Enterprise installation. The CMS is responsible for maintaining a database of information about your BusinessObjects Enterprise system, which other components can access as required. The data stored by the CMS includes information about users and groups, security levels, BusinessObjects Enterprise content, and servers. For more information about the CMS, see BusinessObjects Enterprise Administrator’s Guide.
• UNIX servers that run BusinessObjects Enterprise must have a fixed host name. Root privileges are required to set or modify a fixed host name on the system.
• Installing BusinessObjects Enterprise should not use root privilege. Ask UNIX administrator to create a user account for BusinessObjects Enterprise and perform a user install of BusinessObjects Enterprise.
• Ensure that your database client and server are set up to use Unicode character encoding (such as UTF-8). Consult your database documentation to determine the settings required for a Unicode configuration.
• When installing Oracle database server, server needs to be configured to use Unicode encoding for the character data types.
• The BusinessObjects Enterprise will be connected to a Weblogic application server. The Weblogic application server must be able to communicate with all BusinessObjects Enterprise machines. This communication is enabled by the BusinessObjects Enterprise SDK, which must be installed and configured on the Weblogic application server. In this case, the BusinessObjects Enterprise Java SDK must be installed.
Note:
• Make sure that Weblogic application server has the JDK on it, you will need to install it before installing BusinessObjects Enterprise SDK.
Checking for required commands and utilities
In order for the install setup program to run correctly, the following commands and utilities must be installed on your Solaris 10 system:
/bin/sh
Pwd
read
touch
uname
expr
hostname
sed
Awk
chown
grep
tail
tar
Id
dirname
Gzip
sty
ulimit
which
These relatively standard commands and utilities should be available on most UNIX distributions. However, if for any reason one of them is not available on your system, download and install a version appropriate to your system.
Additionally, these commands and utilities must be accessible in the PATH environment variable of the user account that you use when installing BusinessObjects Enterprise.
Important
Proper verification of both install privileges as well as connect strings need to performed.For Oracle Connectivity make sure that SQL*PLUS can be used to connect to the database.
Components installation before BusinessObjects XI R2 Install
Several components need to be installed before BusinessObjects Enterprise system can be installed. Here is the list that needs to be followed:
1. Installing Oracle Net Client 9.2
Note: Oracle Net Client 9.2 works as tested. Even though the BO XI R2 supported platforms document lists Oracle Net Client 10.2 as supported, there are issues using 10.2 client (64bit). It is recommended to use Oracle Net Client 9.2 with /lib32 set within the .profile
Follow the instruction below to install oracle 9i (9.2.0.6) client on application server.
· Login to application server usplgmhsras001/usplgmhsras002 with “Vbobje” id
· cd /usr/local/oracle/product.
create this directory if not exist.
· untar "9.2.0.6_client.tar” file
cd /usr/local/oracle/product
tar –xvf 9.2.0.6_client.tar
Validation:
With the Vbobje id, run sqlplus, should see the output like below:
SQL*Plus: Release 9.2.0.6.0 - Production on Wed May 23 16:03:53 2007
Copyright (c) 1982, 2002, Oracle Corporation. All rights reserved.
Enter user-name:
Vbobje unix id profile update:
Update Vbobje .profile file with the following entries: (if it’s not updated earlier)
ORACLE_HOME=/usr/local/oracle/product/9.2.0
export ORACLE_HOME
TNS_ADMIN=/var/opt/oracle
export TNS_ADMIN
LD_LIBRARY_PATH=$ORACLE_HOME/lib32
export LD_LIBRARY_PATH
ORACLE_SID=ORCL
export ORACLE_SID
PATH=$ORACLE_HOME/bin:/usr/j2se/bin:$PATH
export PATH
LANG=en_US.UTF-8
LC_ALL=en_US.UTF-8
export LANG LC_ALL
export BOBJE_ENV_SOURCED=""
. $HOME/bobje/bobje/setup/env.sh
tnsnames.ora file update:
· cd /var/opt/oracle
create this directory if not exist.
· Copy the tnsnames.ora file from /usr/local/oracle/product/9.2.0/ to /var/opt/oracle/ and modify the entries mention below:
PreProd / Production:
Database sid name
Database SID VIP
ORCL =
(DESCRIPTION =
(ADDRESS_LIST =
(ADDRESS =
(PROTOCOL = tcp)
(HOST = ORCL)
(PORT = 1521)
)
)
(CONNECT_DATA =
(SID = ORCL)
)
)
Validation:
With the Vbobje id, run
· sqlplus bobje/bobje@ORCL
Should be able to SQL > prompt
· on sql prompt run the following select query
SQL> select name from v$database;
Output should look like this:
NAME
---------
ORCL
1. Setting up an empty database for CMS
2. Setting up an empty database for auditing
3. Creating an account, a home directory and a login environment for BOE installation
4. Providing and verifying connectivity to the CMS database
5. Installing the Java SDK
6. Accessing Weblogic Administration Console. It requires account and password
Setting up an empty database for CMS
BusinessObjects Enterprise requires a database (or Oracle schema) to store information about the system and its users. An existing Oracle 10g database will be used.
Database administrator must create a new database on database server before BusinessObjects Enterprise installation. The database used only for BusinessObjects Enterprise , and not contain other tables.Create a new database, create a new user account and password for the database that will be used by BusinessObjects Enterprise. Ensure that the new account has permission to create, modify, and delete tables and create procedures so that BusinessObjects Enterprise can modify the database as required. Write down name of the database, the user account, and the password. They will be used in BusinessObjects Enterprise installation script.
Name the new database (hisrepcmpldb.iweb.gm.com, instance: hisrepcm), and create a new user account (bobje), however, this naming convention is not required.
Ensure that the database server is set up to use Unicode character encoding (such as UTF-8). Consult your database documentation to determine the settings required for a Unicode configuration. For Oracle database servers, during installation you need to configure the server to use Unicode encoding for the character data types.
Setting up an empty database for auditing (if applies)
Create another database schema for auditing. It can share CMS instance. Name the auditing database (ex: bobjeaudit), and create a new user account (ex: bobjeaudit).
Creating an account, a home directory and a login environment
Create a specific user account and group under which the BusinessObjects Enterprise daemons can run. You will log on as this user in order to perform the remainder of the installation procedures. Although it requires root privileges to set up this account, the account itself does not require root privileges. Neither the installation scripts nor BusinessObjects Enterprise itself needs to run as root.Use usual administrative procedures to perform these recommended tasks.
Setting up UNIX system
Create a new group. Create a new user account, and set this user’s primary group to the new group. Assign a secure password to the new user account.
Create the directory where BusinessObjects Enterprise will be installed. By default, the installation will use current directory, that is, the directory you call the install program from, as its base directory for the install. You can override this default, with the directory of your choice at install time. You will see this directory referred to as INSTALLDIR throughout this document.
Set the new user’s HOME directory to the installation directory that you created. When you run the installation script, you choose a “user” installation type so that all of the installed files are confined to the directory that you specify here.
Ensure that the account you created has read, write, and execute permissions on the new HOME directory.
Assign the new user a default login shell, and create or modify the appropriate login script(s) for the user account. In particular, make sure that the login script(s) set up a default login environment that meets these requirements:
The user’s HOME directory must be included in the PATH environment variable.
All of the commands and utilities required by the install setup program must be accessible in the PATH environment variable. For details, see section 10.1.
The user’s login environment must set up the database environment such that the install setup program can access your database client software. Make sure the tnsnames.ora is set correctly. For details, see section 10.2.
Providing and verifying connectivity to the CMS database
To create tables and write data to the new CMS and auditing databases, the installation scripts need to establish a connection to the database server. That is, when you log on to UNIX with the user name from which you will perform the installation, the default shell environment must include the appropriate database environment variables and/or initialization files. Only then can the installation setup program access the CMS database using your database
client software.
The environment variables and/or files required by the installation scripts depend upon the type of database server you are running:
Oracle database is connected through a native connection, the installation searches the current shell for the ORACLE_HOME environment variable. This standard Oracle environment variable must be set in order for the install script to utilize the Oracle client software.
Additional database environment variables must be set in order for the installation script to use the database client software properly. Before running the installation script, test the shell environment of the account from which you will install BusinessObjects Enterprise to verify database connectivity and privileges. See the procedure that corresponds to the database.
The existing database needs to be sourced:
User can modify their own profile and add the command to source their database environment. This method must be done by the user which installs BusinessObjects Enterprise
Note: Consult database documentation and/or database administrator if the account shell environment from which you will install BusinessObjects Enterprise has not yet been set up for database client software, or if you are unable to connect successfully to the database.
Configuring the Java environment variable
After installing the Java SDK you must set the JAVA_HOME environment variable. If your Java web application server installs the Java SDK as part of its installation process, install the application server first, and then set the environment variable.
You need to know the directory path containing your Java SDK bin directory.
To set the JAVA_HOME environment variable on UNIX
1. Log on to the UNIX server with the user account and password which you will use to do your install.
2. Type JAVA_HOME=
3. To confirm that you’ve set the environment variable correctly, type echo $JAVA_HOME.
4. Using a text editor such as vi, add the command to set JAVA_HOME to the login environment for the account from which you will install BusinessObjects Enterprise. Add the command to your .profile file. This ensures that the value of JAVA_HOME is correctly set each time you log on to the account.
Labels:
.ALL.,
ALL,
Business Objects,
Enterprise Software,
Solaris 10,
WebLogic
Subscribe to:
Posts (Atom)















