Wednesday, July 29, 2009
View Points of SOA
1. SOA Benefits (respond quickly and effectively to business change and leverage that change to gain a competitive advantage)
2. IT and Business as Peers (forge peer working relationships between IT and business)
3. Incremental Business Services (mirror business process steps)
4. Business-Smart IT Architects (Business-aware)
5. Opportunities for Services (each business process interaction with an IT asset is a potential location for a service)
6. Measuring Services (allocate IT costs and provide IT justification by correlating the IT costs with business process results
7. service-Oriented Means in the Core (business processes and services at the center of both business design and IT delivery)
8. Proving Business Value of SOA (through business results measurements)
9. Competitive Business Agility (change in business process no longer requires a change to application programming logic)
Characteristics address the degrees of flexibility that will affect architecture decisions (does it relevant to consumers?)
1. Platform
2. Location
3. Protocols
4. Programming Language
5. Invocation Patterns
6. Security
7. Service Versioning
8. Service Model
9. Information Model
10. Data Format
Infrastructure Services
1. Resource Virtualization Services
2. Service-Level Automation and Orchestration
3. Utility Business Services
Enterprise Service Bus (ESB)
1. Transport
2. Quality-of-Service-Based Routing
3. Mediation
4. Web Service Gateway
SOA Enterprise Software Models
1. Industry Models (ebXML, OAGIS, NGOSS, IFX, IFW)
2. Platform-Independent Qealization (XML, XSD, HTTP, SOAP, WSDL, WS-Policy, WS-Resource, WS-Security)
3. Platform-Specific Realization
4. J2EE Realization (EJB, JAX-RPC, WSDL, DOM, SAX, JCA, J2C)
5. Service Integration on WebSphere Application Server
The Information Management Domain
1. Information Management
2. Information Management Services
3. Reengineering Information Management into Services
4. Meta-Data Management
5. Meta-Data Integration
Friday, July 24, 2009
SOA Program Methodology
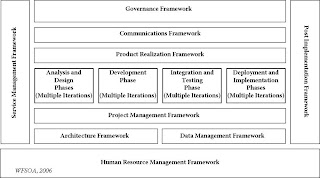
Framework of Governance
Alignment of processes and services with business strategy and results in evolution to a service-oriented enterprise (SOE) (service catelog, registry of services and descriptions)
Framework of Communications
Ensures collaboration of business and technical staff in a continued plan on the endeavor in the firm (dashboar, balanced scorecard, portal)
Framework of Product Realization
Core of established project management methodology.
Framework of Project Management
Ensures the changes in business strategy are applied as appropriate on a project of SOA. Ensures that processes and services are functioning and implemented as planned in the strategy.
Framework of Architect
Ensures evolution from conversion of functions into services, creation of component services and integration into composite servicves, integration of internal applications, internal services and external services, to on-demand servicers in a gradual SOE
Framework of Data Management
Enables implementation of the services, based on access, availability, breadth, and accuracy of data already inthe databases of the applications
Framework of Service Management
Ensures reusability of service. Feasibility of processes and services, and impact on the firm, are evaluated in service management
Framework of Human Resource Management
Enables identification of new and revised responsibilities and roles of business and technical staff on SOA.
Framework of Post Implementation
Enables service and process life-cycle tasks following product realization.
Factors for Enabling Frameworks of Methodology

Factors- Description of Factors
***Business Factors***
Agility, efficiency, and flexibility benefits
- Extent to which benefits of adjusting to business environments drive the program
Financial benefits
- Extent to which benefits of increased revenues or decreased expenses drive the program
Business client participation
- Extent to which business departments consent, contribute, and furnish content and guidance to the program
Competitive, market, and regulatory differentials
- Extent to which competitive, market, and regulatory first-mover edge for the firm drives the program
Customer demand
- Extent to which customer demand for enhanced service from technology drives the program
Culture of innovation
- Extent to which innovation in business and technical practices is encouraged and facilitates the program
Organizational change management
- Extent to which cultural change management is evident in helping business and technical staff embrace the program
Executive sponsorship
- Extent to which senior managers in the firm articulate and evangelize the business criticality of SOA as a strategy and fund the program
Executive business leadership
- Extent to which senior managers in the business units evangelize business criticality of SOA as a strategy
Executive technology leadership
- Extent to which senior managers in the technology departments evangelize the technical and business criticality of SOA as a strategy
Strategic planning
- Extent to which business strategy of SOA is articulated in the firm and is accepted by program staff
Enterprise architecture
- Extent to which formal enterprise architecture contributes to initiation of the program and evolves with processes to an SOA
Focus on improvement of process
- Extent to which improvement of business processes, process integration, and service choreography are the goals of the program
Service orientation
- Extent to which technical and business staff is receptive to principles of service orientation and SOA
Reusability of assets
- Extent to which multiple services using software technologies is a goal of the program
***Procedural Factors***
Control of program
- Extent to which a formal function is evident for guiding and helping the firm in evolution to SOA
SOA center of competency
- Extent to which a centralized team is evident for furnishing SOA expertise help to program staff
Responsibilities and roles
- Extent to which responsibilities and roles of staff on the program are clearly defined for completing project tasks
Education and training
- Extent to which formal skill training on services and SOA is evident for program staff
Knowledge exchange
- Extent to which processes and procedures are evident for informing business and technical staff of progress of the program
Change management
- Extent to which procedures are evident for ensuring optimal resolution of requests for changes in existing processes or services or of requests for new processes or services
Information management
- Extent to which procedures are evident for ensuring data integrity and quality for technical and business functions
Common reference
- Extent to which business and technical terminology is applied consistently by program staff
Naming conventions
- Extent to which naming standards and service versioning are used by program staff
Procurement of technology
- Extent to which a formal function is evident for furnishing quality hardware and software technology to the program in a cost-effective and expeditious manner
Technology firm knowledge capture
- Extent to which program staff captures knowledge from hardware and software technology firms to become independent of the firms
Risk management
- Extent to which procedures are evident for mitigating failure or loss caused by SOA
Standards management
- Extent to which program staff is cognizant of official standards, scope of implementation of the standards by technology firms and standard gap resolution techniques
Infrastructure architecture
- Extent to which procedures are evident for guiding the evolution of technology in a strategy of SOA
Process and service deployment environment
- Extent to which procedures are evident for furnishing software and tools to the development staff on the program
Process and service deployment techniques
- Extent to which procedures are evident in order to ensure the highest quality of deployed technology throughout the program
Service catalog management
- Extent to which procedures for managing a registry or a repository of processes and services are evident on the program
Service management and support
- Extent to which procedures are evident for ensuring service availability and reusability and furnishing metrics on service support Security management- Extent to which procedures are evident for safeguarding access to services
Continuous process improvement
- Extent to which procedures are evident for iterative improvement of existing and new processes
Costing techniques
- Extent to which techniques are evident for costing existing and future SOA product realization and support
Strategy management
- Extent to which procedures are evident for evaluating and improving program strategy of SOA as required
***Technical Factors***
Internal Web services on project
- Extent to which Web services as simple projects contribute to the evolution of SOA
Internal process domain on project
- Extent to which complex Web services applications contribute to the evolution of SOA
Internal SOA domain on project
- Extent to which standards-compliant, internal, and loosely coupled projects contribute to the evolution of SOA
External process domain on project
- Extent to which external tightly coupled and security-sensitive and trusted projects contribute to the evolution of SOA
External SOA domain on project
- Extent to which external standards-compliant, loosely coupled, and security-sensitive and trusted projects contribute to the evolution of SOA
Business process management software
- Extent to which Web Services-Business Process Execution Language (WS-BPEL) software is included in the program
Data tools
- Extent to which data tools supporting eXtensible Markup Language (XML) are included in the program
Middleware
- Extent to which an enterprise service bus (ESB) or traditional middleware technology is included on the program
Platform of key technology firms
- Extent to which the platforms from key technology firms (e.g., BEA, IBM, and Microsoft) are included in the program
Platform specialty tools from platform technology firm
- Extent to which specialty tools of the platform technology firms are included in the program
Proprietary technologies
- Extent to which proprietary software is included in the program
Best-of-class tools
- Extent to which specialty tools from pure-play or third-party technology firms are included in the program XML standard- Extent to which XML is included in
the program
Messaging standards
- Extent to which technology supporting Simple Object Access Protocol (SOAP), SOAP Message Transmission Optimization Mechanism (MTOM), and SOAP with Attachments (SwA) or similar standards is included in the program
Service description and discovery standards
- Extent to which technology supporting Universal Description, Discovery and Integration (UDDI), Web Services Description Language (WSDL), and Web Services-Policy (WS-P) or similar standards is included in the program
Transaction standards
- Extent to which technology supporting Web Services-Composite Application Framework (WS-CAF), Web Services-Choreography Description Language (WS-CDL), and Web Services-Transaction (WS-TX) or similar standards is included in the program
Security standards
- Extent to which technology supporting XML Encryption, XML Signature, Web Services-Federation (WS-F), Web Services-Security (WS-S), and WS-Security Policy (WS-SP) or similar standards is included in the program
User interface standards
- Extent to which user interface tools or Web Services-Remote Portlets (WS-RP) are included in the program Web services best practices- Extent to which Web Services-Interoperability (WS-I) is included in the program
Web services management standards
- Extent to which Service Provisioning Markup Language (SPML) and Web Services-Distributed Management (WS-DM) are included in the program
Responsibilities and Roles of Program Staff for Fulfilling Methodology

Definition
Thursday, July 23, 2009
The LEGO Model of SOA (ZapThink)

1. Interoperable
2. Unbreakable
3. Composable
4. Reusable
Downside of Lego Blocks
1. Lego blocks' strengths pose business challenges for their manufacturer (sale waned over time)
2. Structures built from Lego blocks are only so strong
3. Lego blocks are interoperable with each other, but not with other kinds of toys
4. Lego blocks are for children, but children couldn't build Legoland (architecture is needed)
Lego Blocks and Service Granularity
- Fine-grained Services aren't particularly valuable to the business
- But Services can also be so coarse-grained that ther're too inflexible to meet the needs of the business either
- The optimal granularity for Services generally falls somewhere in the middle
- It makes sense for organizations to build a mix of Services at different levels of granularity
Monday, July 20, 2009
SOA Governance
Simply put, governance sets policies in place, and provides the mechanism to enforce them.
SOA governance life cycle
- Design-Time Governance (defining and controlling of enterprise services to be created in the enterprise, and the creation of policies used to direct and control the implementatin of the enterprise service life cycle)
- Deploy-Time Governance (process of testing and controlling compliance to enterprise policies in order for servics to be deployed in an SOA)
- Run-Time Governance (process of enforcing the adherence to run-time service policies at run time)
- Change-Time Governance (managing services through the cycle of change)
Types of policies used in SOA governance
- Messaging Security
- Access Control Policy
- Conformance to Enterprise Vocabulary and Schema
- Conformance to Technical Standards (WS-I, WSDL, WS-Security, WS-ReliableMessaging)
- Deployment Process
- Versioning Policies
- Discovery Policy
- Privacy Regulations
- Quality of Service (QoS)
- Reliability
- Auditing and Reporting Requirements
- Service Level Agreements (SLAs)
Separate Policy Logic from Business Logic
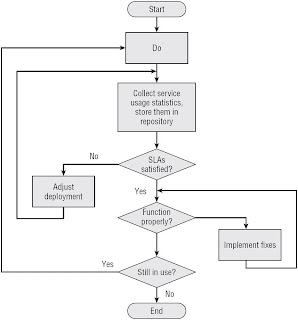
SOA Governance and Service Life Cycle
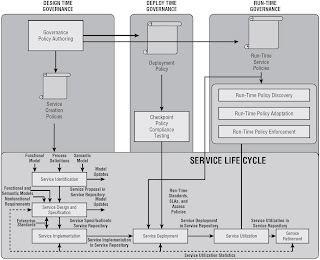
Differentiating Service Policies and Business Processes
Most business processes are based on business rules and workflow, where most run-time governance policies for services are sets of constraints and capabilities that describe how a service and a client interact.
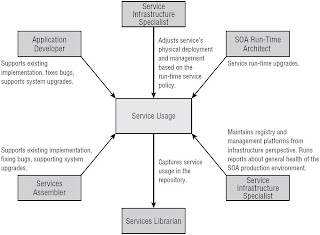
The Service Identifrication Process
Process
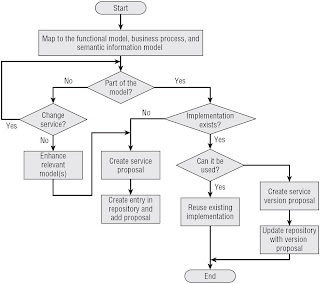
Stakeholders
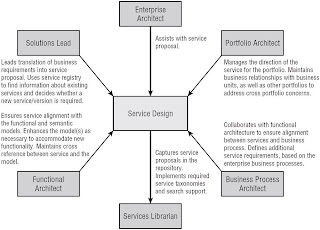
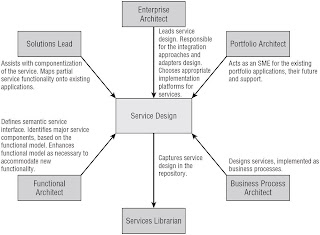
Service Design and Specification Process
Process
Stakeholders
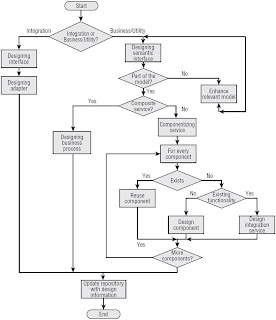
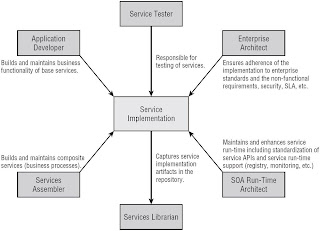
The Service Implementation Process
Process
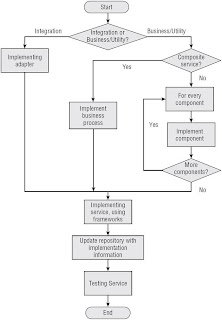
Stakeholders
Deploy-Time Governance
Process
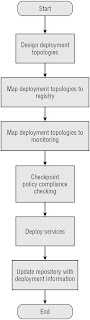
Stakeholders
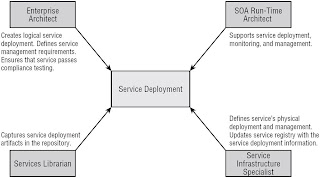
Run-Time Governance
Process
Stakeholders
Developing Enterprise Policy
- Standards compliance
- Common vocabulary
- Naming conventions
- Error handling and suditing
- Run-time service policy authoring
- Genral best practices and blueprints
- Service versioning
SOA governance model (process)
- Requirement Management
(Who collects the requirements? Who tracks changes in requirements? how are new requirements incorporated into the architecture strategy?)
Key procedures
* Requirements definition
* Requirements modification
* Requirements implementation
Mitigating the risks
* Identify valid sources
* Given the reuse levels and complexity within an sOA environment, SOA requirements must be managed on a life-cycle basis
* Requirements tracability
- Architecture Planning
(Who defines SOA architecture? who enforces the use of the sOa architecture? what are the criteria for reusability? who determines the business impact of projects and what metrics do they use? Can you demonstrate the causality between the SOA efforts and business improvements? who pays for a service and support? How much? How do they pay? Per service call, as a percentage of development cost or total cost recovery?)
Key procedures
* SOA architecture design
* SOA service planning
* SOA financial planning
Mitigations
* Increase potential risk areas(highlight closed-loop interactions)
* Interactions are not addressed in terms of timing, who performs them, and how they are performed
* Service performance metrics
- Competency Center Management
(Who owns support? The developers who built the services? A dedicated support team? Should you create an sOa competency center? What resource skills are required? How should it be staffed? How do center personnel work with application teams?)
Key procedures
* Define SOA development support services
* SOA project consulting
Mitigations
* provide necessary people skills
- Business Process Management
(who defines the scope of a business process? How should business process tasks be associated to a web service? who collects business process activity metrics?)
Key procedures
* Business Process Design
* Business Process Development
* Business Process Monitoring
Mitigations
*must be driven by business processes
*leverages client's enterprise business architecture
* Work with enterprise governance
- Service Life Cycle (Who defines naming standards? Who writes services? who tracks the metrics? who publishes the services? who is responsible for assigning service policies?)
Key procedures
* Service Identification and Design
* Service Development, Testing, and Deployment
Mitigations
* Identify proper stakeholders
* HP SOA Governance Tools
- Security Management
(Who builds the security framework for your integration implementation? Who integrates web service security with the rest of the organization's security infrastructure?)
Key procedures
* Security design
* Security implementation
Mitigations
* Align security policies with security design reviews
- Registry / Repository Management
(Which tools are used to build the repository? What will be stored in it and who controls access? How do you enforce maintenance of repository content?)
Key procedures
* Evaluate and select the SOA registry and repository
* Develop SOA registory and repository usage guidelines
Mitigations
* follow usage guidelines
*Review HP SOA Center governance software platform
- Configuration Management
(Who manages the dependencies between services and applications? what are the criteria for creating releases? who builds, manages, and runs the test environment? who determines the timing and cordination of release promotion?)
Key procedures
* SOA environment configuration
* Release management
* Change control
Mitigations
* Identify stakeholdes and coordination methods early
* clear communication plans for configuration management
* Establish standards, methods, and automated tools
- Operations Management
(Who monitors the services? who monitors performance? How should error notification be addressed? who manages issues raised by the use of services across multiple environments?)
Key procedures
* Service monitoring
* Performance management
* Problem management
Mitigations
* leverage coordinator roles
* Identify stakeholders early
Metrics
Closed-loop SOA governance model
- Planning
- Design
- Development
- Testing
- Deployment
- Management
SOA governance model content (within model / process)
- SOA governannce procedures
- Oraanizational structures, roles, & responsibilities
- SOA Policy Compliance Tool
- Supporting Templates
HP SOA Governance Software Tools
Business Technology Optimization for SOA
SOA Governance (SOA Center, HP SOA Solution) (GIF - Governance Interoperability Framework)
- HP SOA Systinet
- HP SOA Policy Enforcer
- HP SOA Registry
SOA Quality (Applications)
- Quality Center with STM (Service Test Management, 70% market share)
- HP Unified Functional Test and Service Test (func testing)
SOA Management (IT operations)
- HP Business Availability Center (BAC) (Enterprise management)
- HP Diagnostics for SOA (Project focus)
Friday, July 17, 2009
SOA Security
- Assigtning Attesting Trust to a Limited Number of Entities



Thursday, July 16, 2009
Designing SOA
The business architecture view is derived from business scenarios, where each scenario is defined by describing the problem, environment, objective, human actors, system actors,a nd roles and responsibilities.
Implementing the Interface Layer
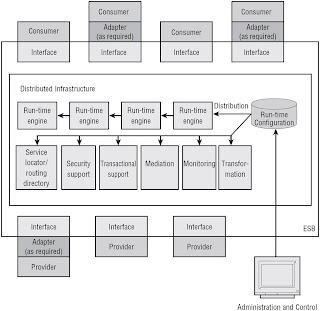
Additional layers for Integration:
- Enterprise Resources and Operational Systems (existing systems)
- Integration Access (access to an existing application's functionality)
- Business components (deployable units of software that provide the (integration) functionality required by the business services
Integration Access Implementations
- Enterprise maturity in the EAI/integration space (existing middleware (messaging infrastructure) can be levferaged)
- Composition of the existing application portfolio (use packaged applications' Web Services)
- Business service implementation platform (e.g. J2EE server prepackage adapters (JCA/J2C)
- Integrated application implementation (Web Service wrappers)
- Type of integration(e.g. JDBC)
Wednesday, July 15, 2009
SOA Design Strategies
- Separation of corcerns
- Architectural views
- Accommodation of change (flexibility)
- Abstraction
- Consistency
- Business derivation
- Facilitation
- Communications
Important Parts of Architecture
- Processes (high-level business functions, often spanning applications or LOBs)
- Services (Modular units of business functionality)
- Integration (Connection to and exposure of existing applications and/or data as services
- Existing systems ( Existing legacy systems, commercial COTS applications, and data that the enterprise wants to leverage
- Documents (high-l.evel units of business information, such as a purchase order, or an EDI document
- Semantics (the underlying meaning of information that is exchanged in processes)
- Transformation (the conversion of information from one format or semantic to another)
- Communications (the ability of services to communicate with each other)
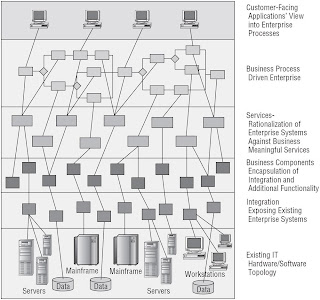
Layered SOA architecture
- Business Process (Enterprise Data [Documents])
- Business Services (Consolidated Data [Semantic Objects])
- Integration Services (Integration Data [Transformation])
- Enterprise Resources (Operational Data [SOR])
SOA aspects of services within an enterprise
- Defining a Service (domain, business, enterprise business process etc.)
- Defining How Services Are Built and Used (Granularity, Type or style of interface, Configuration mechanisms, Other artifacts, Associated information, Dependency management and other patterns)
- Integrating Packaged and Legacy Systems into the Service Environment
- Combining Services into Enterprise Processes
- Specifying the Technology Infrastructure (Communications mechanism, Failover mechanisms, Discovery and location transparency)
- Defining Common Semantics and Data
- Aligning Services with the Business
- Determining How to Use the Architecture
EA and SOA Compared
Business Architecture <-> Business Model
Information Architecture <-> Common Semantics and Data
Technology Architecture <->Service Bus (infrastructure, distributrion, binding, security, performance, etc)
Application Architecture <-> Service, Data, Integration Service, Enterprise Business Process
Software Architecture (4+1 Views)
- Logical View (abstract, platfor, and technology-independent)
- Component View (organized arougn services or service groups)
- Process View (how artifacts assigned to executable processes)
- Physical View (machines, programs, network nodes, hosts, etc)
- Use Cases (in the middle) (capabilities of the system envisioned by end consumer)
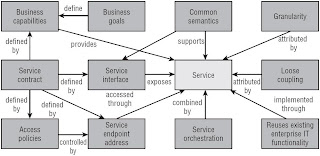
Service Contract Includes:
- Service interface
- Interface documents
- Service policies
- Quality of service (QoS)
- Performance
Good Service Characteristics
- Modularity and granularity
- Encapsulation
- Loose coupling
- Isolation of responsibilities
- Autonomy
- Reuse
- Dynamic discovery and binding
- Stateless
- Self-describing
- Composable
- Governed by policy
- Independent of location, language, and protocol
Levels of Granularity
- Enterprise business processes
- Business services
- Domain services
- Utility services (lower-level services that provide common functionality across the enterprise)
- Integration services (expose existing applications as services)
- External services
- Foundation services (fine-grained capabilities used in higher-level services)
Service Dimensions
- Scope
- Ownership
- Granularity
- Construction
Service Types
- Task services
- Entity services
- Decision services
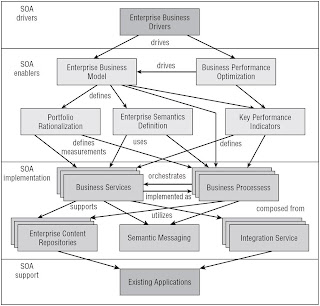
SOA Reference Architecture
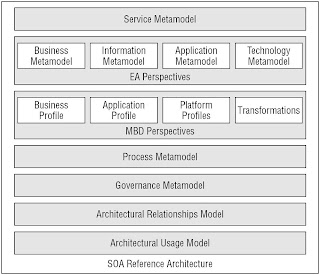
SOA Implementation Methodology
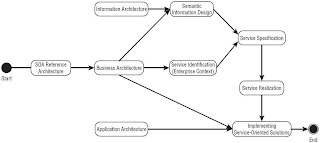
*Business Processes
- A group of logically related (and typical sequenced) activities that use the resources of the organization ot provide defined results.
*Information Design
- The semantic data is not the same as the domain data. It defines the information that must be common between processes.
- The semantic information model defines the messages exchanged by services.
- It is possible to introduce the notion of passing the service execution context around as part of the service invocation "thread". In this case, the service interface operations are massively polymorphic and expressed as:
Service.method (XML context in, XML context out)
*Service Identification
- Instead of attempting to decompose applications, it decomposes entire enterprise IT functionality
- A better decomposition approach is based on the decomposition of the enterprise-wide business model
*Service Specification
Business users need to understand what a service does in business terms, which requires answers to the following questions:
- What does the service provide for prospective clients? This includes a description of what is accomplished by the service, limitations on service applicability and quality of service (QoS), and requirements that the service requester must satisfy to use the service succssfully
- How is the service used? This includes a detailed definition of the content of service requests and responses, the conditions under which particular outcomes occur, and, when necessary, a step-by-step description of processes leaing to those outcomes
Technical users need to know how to implement service operations that require answering the following questions:
- How the interact with services? This specifies a communication protocol, message formats, including serialization techniques and service locations
- What are the service invocation policies? This defines specific requirements for service invocation, (security, SOAP headers, etc)
- What are service QoS guarantees? This specifies the quality-of-service characteristics that the service provides, including response time, throughput, availability, planned maintenance, etc
Service Expectations
Interaction Model
- Information model
- Process (behavioral) model
- Service execution model
Service Constraints
- Business-oriented policies (hours of operation, return policies, etc)
- Infrastructure-oriented policies (security, privacy, manageability, performance, etc)
Service Location
*Service Realization
- Buy
- Outsource (rent)
- Build
Buying Services
- Functional alignment with the overall business model, service decomposition, and service inventory
- usage of the enterprise semantic information model for service interface definitions
- Support for the enterprise service infrastructure, including security, logging, exception handling, and so on
Outsourcing Services
- Designed foruse by customers through the Internet
- Hosted off-premises, not on the customer's premises
- Governed by a service contract
Two common approaches to incorporating SaaS into an overall SOA
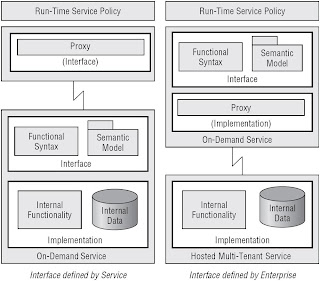
Building Services
- Service Component Architecture (SCA)
- SCA specifies how to create components, combine them, and expose the component assembly as a service
- SCA defines a common assembly mechanism to specify how those components are combined and exposed as a set of services
Service implementation concerns
Service Life Cycle
1. Service identification
2. Service design and specification
3. Service implementation
4. Service deployment
5. Service usage and enhancement
6. Service retirement
SOA Governance includes
- Policies regulating service definition and enhancements, including ownership, roles, criteria, review guidelines, etc
- Identification of roles, responsibilities, and owners
- Policy enforcement that is integrated directly into the service repository (where appropriate)
- Guidelines, templates, checklists, and examples that make it easy to conform to governance requirements
- Review of service interface definitions fornew services and enhancements to existing services
- Architectural review of applications and services to ensure that they conform to the SOA and EA
*The Service Design Process
Top-Down Approaches
- Enterprise System Analysis
- Business Process Model
Bottom-Up Approaches
- Utility Services
- Service Enabling
Middle-Out
- Business Summary (Activities, Artifacts, Repositories, Governance)
- Process Phases (Architectural Context, Business, Desing, Implementation, Test)
Tuesday, July 7, 2009
CMMI-Dev Process Areas
- Requirements Management (REQM)
* Specific Goal 1: Requirements are managed and inconsistencies with project plans and work products are identified
- Project Planning (PP)
* SG1: Establish Estimate
* SG2: Develop a Project Plan
* SG3: Obtain Commitment to the Plan
- Project Monitoring and Control (PMC)
* SG1: Monitor Project Against Plan
* SG2: Manage Corrective Action to Closure
- Supplier Agreement Management (SAM)
* SG1: Establish Supplier Agreements
* SG2: Satisfy Supplier Agreements
Support
Basic Support Process Areas
- Configuration Management (CM)
* SG1: Establish Baselines
* SG2: Track and Control Changes
* SG3: Establish Integrity
- Measurement and Analysis (MA)
* SG1: Align Measurement and Analysis Activities
* SG2: Provide Measurement Results
- Process and Product Quality Assurance (PPQA) (L2)
* SG1: Objectively Evaluate Processes and Work Products
* SG2: Provide Objective Insight
Advanced Support Process Areas
- Decision Analysis and Resolution (DAR) (L3)
* SG1: Evaluate Alternatives
- Causal Analysis and Resolution (CAR) (L5)
Process Management
Basic Process Areas
- Organizational Process Focus (OPF) (L3)
* SG1: Determine Process Improvement Opportunities
* SG2: Plan and Implement Process Imporvements
* SG3: Deploy Organizational Process Assets and Incorporate Lessons Learned
- Organizational Process Definition (OPD) (L3)
* SG1: Establish Organizational Process Assets
- Organizational Training (OT) (L3)
* SG1: Establish an Organizational Training Capability
* SG2: Provide Necessary Training
Advanced Process Areas
- Organizational Process Performance (OPP) (L4)
- Organizational Innovation and Deployment (OID) (L5)
Advanced Project Management
- Risk Management (RSKM) (L3)
* SG1: Prepare for Risk Management
* SG2: Identify and Analyze Risks
* SG3: Mitigate Risks
- Integrated Project Management (IPM) (L3)
* SG1: Use the Project's Defined Process (tailored from standard processes)
* SG2: Coordinate and Collaborate with Relevant Stakeholders
- Quantitative Project Management (QPM) (L4)
Engineering
Process Areas
- Requirements Development (RD) (L3)
* SG1: Develop Customer Requirements
* SG2: Develop Product Requirements
* SG3: Analyze and Validate Requirements
- Technical Solution (TS) (L3)
* SG1: Select Product Component Solutions
* SG2: Develop the Design
* SG3: Implement the Product Design
- Product Integration (PI) (L3)
* SG1: Prepare for Product Integration
* SG2: Ensure Interface Compatibility
* SG3: Assemble Product Components and Deliver the Product
- Verification (VER) (L3)
* SG1: Prepare for Verification
* SG2: Perform Peer Reviews
* SG3: Verify Selected Work Products
- Validation (VAL) (L3)
* SG1: Prepare for Validation
* SG2: Validate Product or Product Components
CMMI
Capability Level 4 Must Satisfy:
- All Goals in Level 4
And

Wednesday, July 1, 2009
WebSphere AS Architecture

WAS-XD improves system availability, maintaining multiple instances of key components so that services can be switched from one server to another.
Edge Components offer an efficient and economic means of hosting web-accessible content and providing Internet access. The software typically runs on machines that are in proximity to the boundary between an enterprise intranet and the Internet.
Edge Components include the caching proxy and load balancer, which help administrators to provide improved levels of service to internal and external users with access to documents on enterprise server machines.
A cluster is a logical arrangement of application server processes designed for workload balancing. Application servers that are part of a cluster are "members" of that cluster and must have identical application components deployed on them. Cluster members are not required to share any configuration data.
Cluster members can be situated on a single node (vertical cluster), over a number of nodes (horizontal cluster), or a mixture of the two.
Managed Servers or Processes
- Deployment Manager (Network Deployment Only)
- Node Agent (Network Deployment Only)
- Application Server (Base and Network Deployment)
- JMS Server (Network Deployment Only)
Network Deplyment
- Multiple WAS instances
1. Application Servers (multiple instances from a single installation of WAS)
2. Deployment Manager (multiple instances from a single installation of Network Deployment)

Oracle AS 10g
OracleAS Infrastructure (clustering) Categories
Products


























